Contents:
A TP-Link Archer A21 (AX1800) consumer-grade WiFi router vulnerability has been used by Mirai botnet to launch DDoS attacks against IoT devices. The flaw in the TP-Link Archer AX21 firmware was discovered back in December 2022, and the company released a patch in March.
However, recent attacks show a new variant of the Mirai botnet exploiting the flaw (CVE-2023-1389) to gain access to devices. Researchers said they first saw activity targeting devices in Eastern Europe, but detections have now spread worldwide. In order to execute binary payloads for various system architectures, the attackers make HTTP requests to Mirai command-and-control (C2) servers using the TP-Link flaw.
Vulnerability Specifics
An unauthenticated command injection vulnerability exists in the localeAPI endpoint (in the web management interface). Starting on April 11th, researchers began seeing notifications that a threat actor had started to publicly exploit this vulnerability.
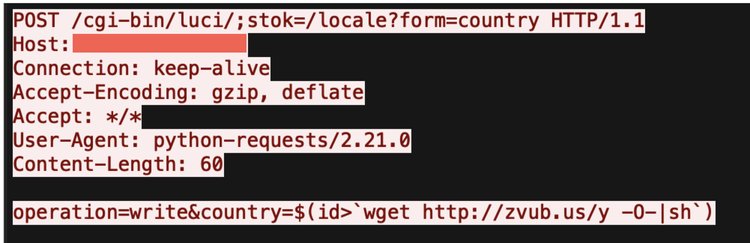
In order to determine the appropriate payload for the target system architecture, binary payloads are downloaded and then executed using brute-force methodology. Upon finding the appropriate binary and installing the payload, the host becomes fully infected and establishes a connection with the Mirai C2.
Seeing this CVE being exploited so quickly after the patch being released is a clear demonstration of the decreasing “time-to-exploit” speed that we continue to see across the industry.
TP-Link developed and released a patch. Applying this patch is the only recommended action to address the vulnerability and stay safe from cyberattacks. All users of the TP-Link Archer AX21 Wi-Fi router are urged to do so as soon as possible.
Mirai Botnet in Review
As part of a defense racket against DDoS attacks, three Minecraft players in 2016 released the botnet that infects IoT devices running on ARC processors. Cybercriminals assembled their own Mirai botnets after someone posted the code online. The original coders pleaded guilty to federal charges and cooperated with the FBI in 2017.
Since then, the malware has expanded its methods of gaining initial access beyond the use of known default credentials to include exploiting vulnerabilities in targets. You can read an in-depth analysis on Mirai botnet here.
Back in February 2023, a new variant of the Mirai-based Medusa DDoS botnet was discovered in the wild, equipped with a ransomware module and a Telnet brute-forcer.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security