UPDATE
More than 80 global eCommerce sites have been uncovered that were actively compromised by Magecart groups.
Magecart, a loose affiliation of attack groups responsible for the payment-card attacks on Ticketmaster, Forbes, British Airways, Newegg and others, typically insert virtual credit-card skimmers, also known as formjacking, into a web application (usually the shopping cart), and proceed to steal credit card information to sell on the black market.
According to research released Wednesday from the Aite Group and Arxan Technologies, a quarter (25 percent) of the sites discovered were “large, reputable brands in the motorsports industry and luxury apparel.” In all, the compromised sites were spread out across the United States, Canada, Europe, Latin America and Asia.
To conduct the research, Alissa Knight, cybersecurity analyst for Aite Group, used a source-code search engine that scoured the web for obfuscated JavaScript that she found in repeating patterns of previously published Magecart breaches.
After 2.5 hours of initial research, more than 80 compromised eCommerce sites globally were found actively sending credit-card numbers to off-site servers under the control of the Magecart groups.
Outdated Magento Versions
The research showed that the most common similarity across the 80 sites was the use of Magento, all of which are running old versions that are vulnerable to published exploits.
“The latest version of Magento Community Edition is version 2.1.7,” according to the research. “Many of the compromised sites are running version 1.5, 1.7, or 1.9. The arbitrary file upload, remote code-execution and cross-site request forgery vulnerabilities all affect Magento version 2.1.6 and below.”
One of the many vulnerabilities many of these sites were vulnerable to is related to the way Magento handles video content and the retrieval of the preview image.
“When adding Vimeo video content to a new or existing product, the application will automatically retrieve a preview image for the video via a POST request that takes a remote image URL parameter,” Knight explained. “The request method can be changed to GET, so the request can be sent as … “http://victim/magento2/admin_1bcbxa/product_video/product_gallery/retrieveImage/?remote_image=https://i.vimeocdn.com/video/438193448_640.jpg.”
If a URL points to an invalid image (a PHP file for example), the application will respond with an error, but the file will be downloaded regardless.
“The application saves the file to validate the image but will not remove it if the validation fails,” Knight said. “The file will be saved to ‘/pub/media/tmp/catalog/product/<X>/<Y>/<original filename>,’ in which X and Y are the first two characters of the file name. A PHP script proof of concept could be <?php echo hell_exec($_GET[‘cmd’]); ?> and accessed as http://<ip of victim>/magento2/pub/media/tmp/catalog/product/_/h/.hshell.php?cmd=whoami.”
In addition to the outdated software, none of the sites had tamper detection or code obfuscation implemented, either.
“Adversaries are able to easily debug and read a web app’s JavaScript or HTML5 in plain text,” Knight said in the research. “Once the web app code is understood, malicious Javascript is then inserted into the web pages of target servers that delivers the web checkout form. Once weaponized, these credential pages will simultaneously send a consumer’s credit-card information to an off-site server under the control of the Magecart group while also allowing the compromised site to process the credit card so the consumer and the organization is unaware of the theft.”
Malicious JavaScript can be encoded using Base64, XML, Hex or others in order to make the malicious code unreadable. The report pointed out that this obfuscation hides the malicious code in plain sight, since most administrators don’t look in their source code for obfuscated JavaScript, let alone decode it using a Base64 decoder to determine if its legitimate.
“Magecart groups have even begun getting smarter by using timing as well as code-signing to detect analysis and tampering of their malicious code once it’s injected into a web form,” according to the report.
Beyond the Dark Web
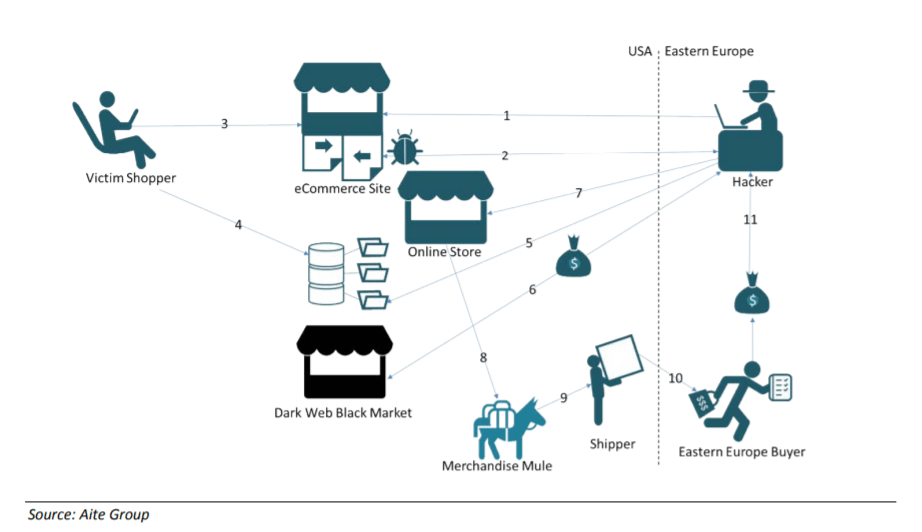
The research also uncovered a “reshipping” arm of Magecart’s monetization activities. Beyond simply selling the “fullz” – a term used by carding groups to refer to full primary account number, card holder contact information, credit card number, CVC and expiration date – attackers can also purchase merchandise on legitimate online shopping sites and resell it.
To launder these fraudulent transactions, the goods are shipped to pre-selected merchandise mules, according to the research.
“To recruit merchandise mules, the attacker posts jobs that offer people the ability to work from home and earn large sums of money to receive and reship merchandise purchased with the stolen credit-card numbers,” the report said.
The mules then work with local shippers willing to receive under-the-table pay to send goods to eastern European addresses, which are in countries on the sanctioned shipping destinations for the Office of Foreign Assets Control (OFAC) regulations. Once there, the merchandise is fenced to local buyers, which the attackers also profit from.
Telemetry from Arxan meanwhile shows that an estimated one-fifth (20 percent) of websites hit by Magecart become reinfected within five days of remediating the original problem.
“The push toward a modern user experience creates a lucrative attack surface inside the web content delivered via browser and mobile,” said Aaron Lint, chief scientist and vice president of research at Arxan, in the report. “Any interface which takes user input becomes a target for exfiltration. Additionally, the widespread use of third-party components has created a supply chain, where an attacker can easily compromise thousands of sites with a mere few lines of code.”
The affected organizations were officially notified in cooperation with the FBI’s cyber-division, according to the report.
Aug. 29, Noon ET: After this article was published, it came to Threatpost’s attention that the information on Magecart’s reshipping activities was previously outlined in a RiskIQ/Flashpoint report last year.
Interested in more on the internet of things (IoT)? Don’t miss our free Threatpost webinar, “IoT: Implementing Security in a 5G World.” Please join Threatpost senior editor Tara Seals and a panel of experts as they offer enterprises and other organizations insight about how to approach security for the next wave of IoT deployments, which will be enabled by the rollout of 5G networks worldwide. Click here to register.