VMware Carbon Black Threat Report finds hackers using more aggressive and destructive tactics
Tech Republic Security
AUGUST 4, 2020
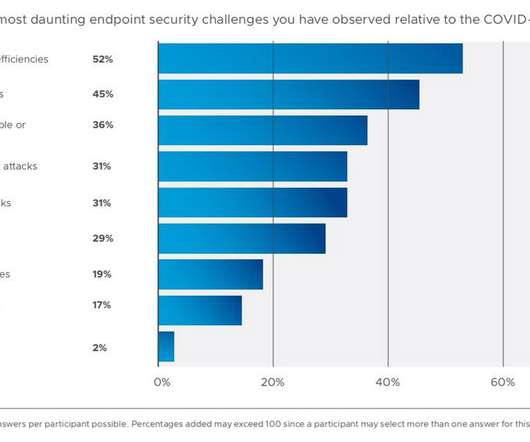
Security firm recommends digital distancing for devices and more collaboration between IT and security teams to harden the attack surface.




































Let's personalize your content