Why No HTTPS? The 2021 Version
Troy Hunt
AUGUST 12, 2021
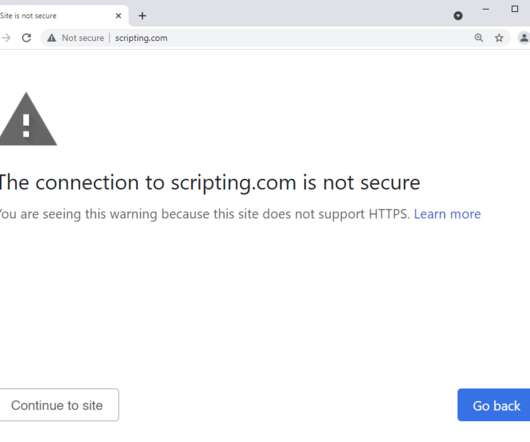
More than 3 years ago now, Scott Helme and I launched a little project called Why No HTTPS? It listed the world's largest websites that didn't properly redirect insecure requests to secure ones. We updated it December before last and pleasingly, noted that more websites than ever were doing the right thing and forcing browsers down the secure path.






































Let's personalize your content