WEIS 2021 Call for Papers
Schneier on Security
FEBRUARY 18, 2021
The 20th Annual Workshop on the Economics of Information Security (WEIS 2021) will be held online in June. We just published the call for papers.

Schneier on Security
FEBRUARY 18, 2021
The 20th Annual Workshop on the Economics of Information Security (WEIS 2021) will be held online in June. We just published the call for papers.

Tech Republic Security
FEBRUARY 18, 2021
In a webinar Wednesday, former US Homeland Security director Christopher Krebs also suggested organizations have COVID workforce coordinators and that cloud mail providers activate MFA by default.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
FEBRUARY 18, 2021
Virginia is about to get a data privacy law , modeled on California’s law.
Bleeping Computer
FEBRUARY 18, 2021
Attackers are abusing Google's Apps Script business application development platform to steal credit card information submitted by customers of e-commerce websites while shopping online. [.].

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Boulevard
FEBRUARY 18, 2021
Oracle Corp. stands accused of selling analytics to Chinese police forces that’s being used to hunt down political dissidents and lock up Uyghur Muslims. The post Oracle is Said to Help China Find Dissidents and Jail Minorities appeared first on Security Boulevard.
Security Affairs
FEBRUARY 18, 2021
PaloAlto Network warns of the WatchDog botnet that uses exploits to take over Windows and Linux servers and mine cryptocurrency. Security researchers at Palo Alto Networks uncovered a cryptojacking botnet, tracked as WatchDog, that is targeting Windows and Linux systems. WatchDog is one of the largest and longest-lasting Monero cryptojacking operations uncovered by security experts, its name comes from the name of a Linux daemon called watchdogd.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

We Live Security
FEBRUARY 18, 2021
The first instance of malicious code native to Apple Silicon M1 Macs emerged a month after the release of devices equipped with the company’s in-house CPUs. The post Malware authors already taking aim at Apple M1 Macs appeared first on WeLiveSecurity.

Bleeping Computer
FEBRUARY 18, 2021
Microsoft announced today that the SolarWinds hackers could gain access to source code for a limited amount of components used by Azure, Intune, and Exchange. [.].

The Hacker News
FEBRUARY 18, 2021
One of the first malware samples tailored to run natively on Apple's M1 chips has been discovered, suggesting a new development that indicates that bad actors have begun adapting malicious software to target the company's latest generation of Macs powered by its own processors.

CyberSecurity Insiders
FEBRUARY 18, 2021
Kia Motors America is experiencing a nationwide outage because of a ransomware attack and confirmed sources say that the car maker was targeted by DoppelPaymer gang that is demanding $20 million to decrypt the database. In a media update released early this morning, the South Korean company stated that the nationwide IT outage resulted in disruption of services related to payment systems, UVO Link app, phone services, owner portal, internal sites and dealership link.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Security Boulevard
FEBRUARY 18, 2021
While there are undoubtedly many major challenges within the world of cybersecurity, one of the principal roadblocks to the implementation of effective data security is the lack of skilled cybersecurity practitioners. In a November 2019 report, the International Information System Security Certification Consortium, (ISC)² suggested that the cybersecurity workforce needs to increase by 62 percent […].

Quick Heal Antivirus
FEBRUARY 18, 2021
Cyberpunk 2077 has been one of the most anticipated releases in gaming history. In development since 2012 and. The post Ransomware attacks erupt via Cyberpunk 2077 appeared first on Quick Heal Blog | Latest computer security news, tips, and advice.

Security Boulevard
FEBRUARY 18, 2021
Jamaica just experienced a massive data breach that exposed the immigration and COVID-19 records of hundreds of thousands of people who visited the island over the past year. Much of the information found on the exposed server was from Americans. … Read more. The post Hundreds of Thousands Immigration and COVID Records Exposed in Jamaica appeared first on DivvyCloud.

The State of Security
FEBRUARY 18, 2021
The United States Department of Justice has charged three North Korean computer programmers with a range of cyber attacks that made headlines around the world. The men – 31-year-old Jon Chang Hyok, Kim Il, 27, and 36-year-old Park Jin Hyok – are alleged to have been part of North Korea’s Reconnaissance General Bureau (RGB), known […]… Read More.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
FEBRUARY 18, 2021
The injection of sophisticated malware into SolarWinds software was attributed to Russian Intelligence. An unrelated attack, made possible by exploiting a vulnerability in SolarWinds software, is being attributed to Chinese hackers. Periodically, other breaches are attributed to North Korean and Iranian hackers. However, nations do not often admit to being behind hacking activities.

Identity IQ
FEBRUARY 18, 2021
With the digital world now deeply rooted in the fabric of society, we are increasingly living double lives. There is our immediate, physical existence – and there is our digital identity. Most people are more familiar with the first. But as our information and behavior go digital, a more complete picture of who we are emerges. In a nutshell, your digital identity encompasses all the information that exists about you in digital form.

Hot for Security
FEBRUARY 18, 2021
In tax-related fraud, a criminal files a tax return in your name, using your stolen personal information, including your Social Security number. Here we reveal some of the most common tactics and fake documents fraudsters use to trick people. Here are some of the signs you might be a victim of financial theft: You get a letter from the IRS inquiring about a suspicious tax return you did not file.
The Hacker News
FEBRUARY 18, 2021
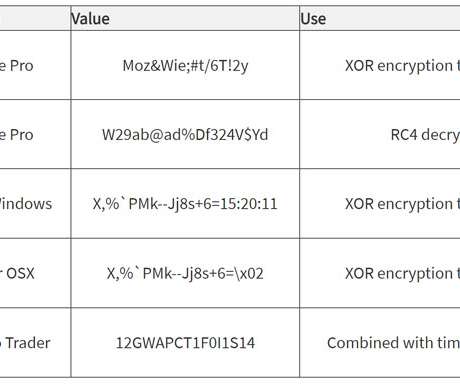
The U.S. Department of Justice (DoJ) on Wednesday indicted three suspected North Korean hackers for allegedly conspiring to steal and extort over $1.3 billion in cash and cryptocurrencies from financial institutions and businesses.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
Security Boulevard
FEBRUARY 18, 2021
As 2020 wound to a close, the year’s end marked a major milestone in strengthening the security of Internet of Things (IoT) devices and systems. In December, the IoT Cybersecurity Improvement Act was signed into law, raising the priority of cybersecurity across a variety of industries and use cases. The new law is designed to. The post New IoT Legislation Means Advance Planning is Key appeared first on Security Boulevard.
SC Magazine
FEBRUARY 18, 2021
A graph representing the NIST Phish Scale scoring methodology. (NIST). Officials from the National Institute of Standards and Technology (NIST) this week teased future improvements to the agency’s recently introduced “Phish Scale” measurement system, which helps companies determine whether phishing emails are hard or easy for their employees to detect.

CSO Magazine
FEBRUARY 18, 2021
As the threat landscape continues to evolve, security environments grow in complexity, and the skills gap widens, security teams need to come up with new ways to increase efficiency and productivity in order to keep up. One such way is through security automation, which empowers security teams to focus on high-impact initiatives by eliminating excess noise, reducing low-brain high-time tasks, and increasing alert fidelity.
Threatpost
FEBRUARY 18, 2021
A malicious adware-distributing application specifically targets Apple's new M1 SoC, used in its newest-generation MacBook Air, MacBook Pro and Mac mini devices.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

PCI perspectives
FEBRUARY 18, 2021
Today, the PCI Security Standards Council (PCI SSC) published version 1.1 of the PCI Secure Software Lifecycle (SLC) Standard and its supporting program documentation. The PCI Secure SLC Standard is one of two standards that are part of the PCI Software Security Framework (SSF). It provides security requirements and assessment procedures for software vendors to integrate into their software development lifecycles and to validate that secure lifecycle management practices are in place.

Bleeping Computer
FEBRUARY 18, 2021
The Federal Bureau of Investigation (FBI) has warned of the harsh consequences of telephony denial-of-service (TDoS) attacks and has also provided the steps needed to mitigate their impact. [.].

Graham Cluley
FEBRUARY 18, 2021
Facebook - angry that the Australian government wants it and other tech giants to pay for content reposted from media outlets - has blocked users in Australia from sharing or viewing news content on the platform. And in characteristic style, they've made a right pig's ear of it. The drongos.

SC Magazine
FEBRUARY 18, 2021
Along with the Pirrit Mac adware identified earlier this week, researchers from Red Canary identified Thursday a different malware strain (Jon Rawlinson/CC BY 2.0)). In just three months, hackers have debuted at least two strains of malware designed to attack Apple’s new M1 chip. Noted Mac security researcher Patrick Wardle published a blog Feb. 14 noting that a Safari adware extension that was originally written to run on Intel x86 chips was revamped to run on the new M1 chips.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Bleeping Computer
FEBRUARY 18, 2021
NVIDIA is purposely crippling the Ethereum mining power of their upcoming GeForce RTX 3060 GPU by 50% to increase inventory for gamers. [.].

SC Magazine
FEBRUARY 18, 2021
Law enforcement officials from Ukraine, France and the U.S. this month cracked down on the Egregor ransomware gang, shutting down its leak website, seizing computers and arresting individuals who are allegedly linked to ransomware attacks that netted $80 million in illicit profits from more than 150 victimized companies. Early reports indicated that the apprehended suspects are affiliates who allegedly purchased access to the Egregor ransomware-as-a-service (RaaS) on the dark web, agreeing to sh

Security Boulevard
FEBRUARY 18, 2021
New Capital Positions Company for Accelerated Growth in Access Control Management for On-Prem and Cloud Environments; Increases Functionality Across IAM and Expands Managed Service Capabilities Hoboken, New Jersey – February 18, 2021 – SPHERE, a woman-owned cybersecurity business focused on providing best-of-breed software and services for access governance across data, platforms and applications, today.

SC Magazine
FEBRUARY 18, 2021
The Apple M1 chip. (Apple). Apple released substantial updates Thursday to its Platform Security Guide – the first revision since April, and the first in the era of Apple’s self-designed M1 chips. The guide is traditionally a critical resource to anyone researching or wrangling security on Apple products, with the most thorough official explanation of product security capabilities.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content