Customer Care Giant TTEC Hit By Ransomware
Krebs on Security
SEPTEMBER 15, 2021
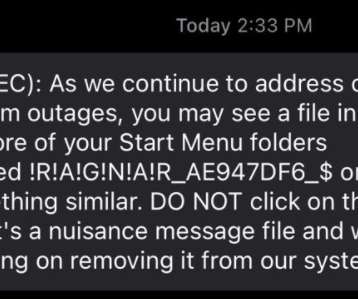
TTEC , [ NASDAQ: TTEC ], a company used by some of the world’s largest brands to help manage customer support and sales online and over the phone, is dealing with disruptions from a network security incident resulting from a ransomware attack, KrebsOnSecurity has learned. While many companies have been laying off or furloughing workers in response to the Coronavirus pandemic, TTEC has been massively hiring.








































Let's personalize your content