Linux malware sees 35% growth during 2021
Bleeping Computer
JANUARY 15, 2022
The number of malware infections on Linux-based IoT (internet of things) devices rose by 35% in 2021 compared to the previous year's numbers. The principal goal was recruiting devices to be part of DDoS (distributed denial of service) attacks. [.].









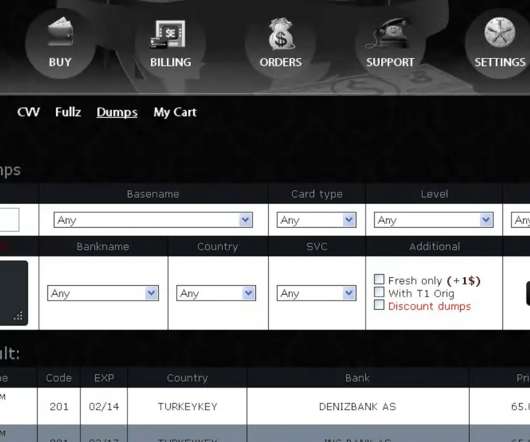










Let's personalize your content