Colonial Pipeline, Darkside and Models
Adam Shostack
MAY 15, 2021
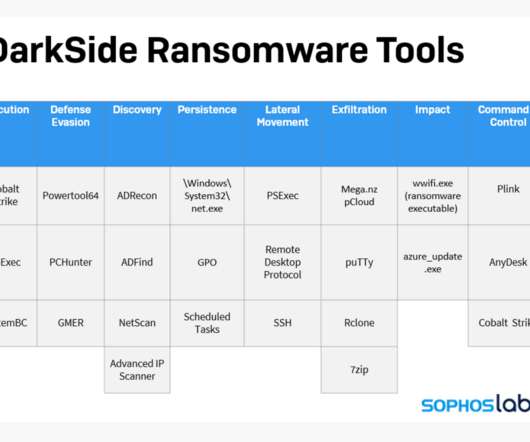
The Colonial Pipeline shutdown story is interesting in all sorts of ways, and I can’t delve into all of it. I did want to talk about one small aspect, which is the way responders talk about Darkside. Blog posts from Sophos and Mandiant seem really useful! Information sharing is working, and what the heck does a Cyber Review Board have left to do?



























Let's personalize your content