Contents:
The pro-Russian hacktivist group ‘KillNet’ claims large-scale distributed denial-of-service (DDoS) attacks on the websites of several major airports in the United States, making them inoperable.
Travelers are unable to connect and receive updates about their scheduled flights or book airport services because the servers hosting these sites are being overloaded by garbage requests as a result of the DDoS attacks.
The Hartsfield-Jackson Atlanta International Airport (ATL), one of the country’s busiest air traffic hubs, and the Los Angeles International Airport (LAX), which is intermittently offline or very slow to respond, are two notable examples of airport websites that are unavailable.
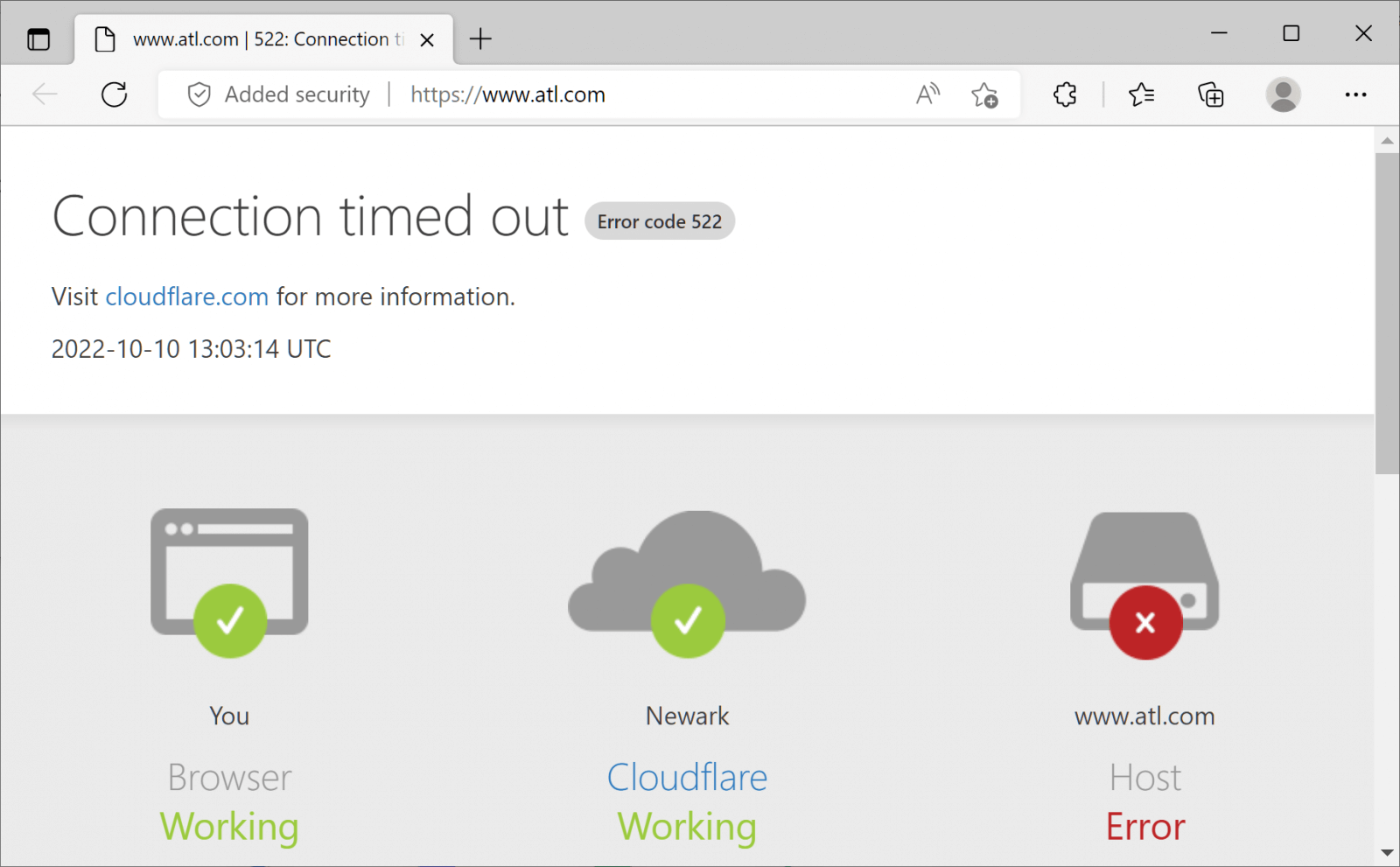
Atlanta Airport website (Source)
Chicago O’Hare International Airport (ORD), Denver International Airport (DIA), Phoenix Sky Harbor International Airport (PHX), Orlando International Airport (MCO), as well as some in Kentucky, Mississippi, and Hawaii, are some other airports that are returning database connection errors.
How Does the Hacktivist Group Attack?
KillNet announced the domains about to be taken down yesterday on its Telegram channel, where hacktivist members and volunteers gather to acquire new targets.
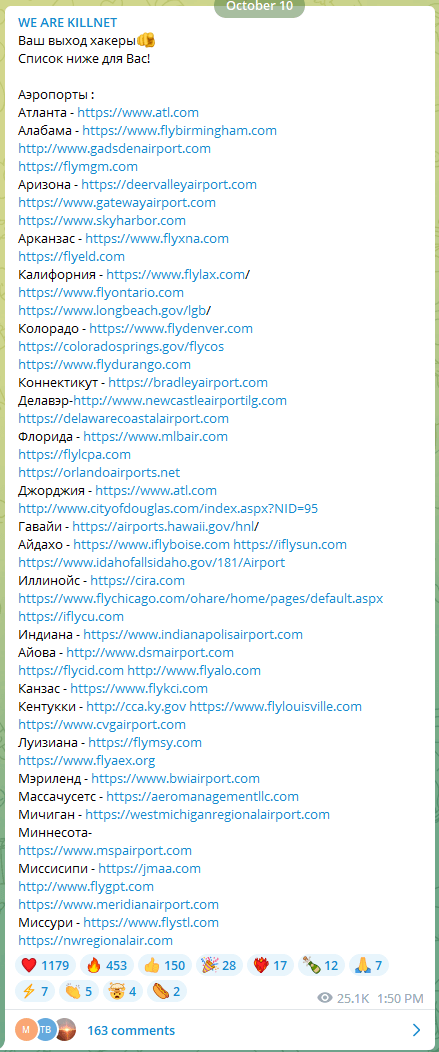
The list of targets (Source)
According to Bleeping Computer, they are using customized software to create bogus requests and garbage traffic that is directed at the targets in an effort to exhaust their resources and block legitimate users from using them. Although the DDoS attacks in this instance do not affect flights, they still negatively impact the functioning of a huge economic sector and pose a risk of delaying or disrupting related services.
KillNet has previously targeted countries that supported Ukraine, such as Romania and Italy, and its “sub-group” Legion has targeted key Norwegian and Lithuanian entities. As the conflict in Ukraine evolves, pro-Russian threat actors and hacktivists are attempting to increase their retaliatory cyberattacks against neuralgic organizations in the Western world.
At the beginning of October, the Finnish Security Intelligence Service (SUPO) warned of a highly likely intensification of cyberespionage activities conducted by Russia-linked threat actors over the winter.
Moreover, a greater number of threat actors are exploiting the event of the Russian invasion in Ukraine to launch not only DDoS, but also phishing and malware cyberattacks against Eastern European and NATO countries, as my colleague Andra explained in this article in March.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










