More on NSO Group and Cytrox: Two Cyberweapons Arms Manufacturers
Schneier on Security
DECEMBER 20, 2021
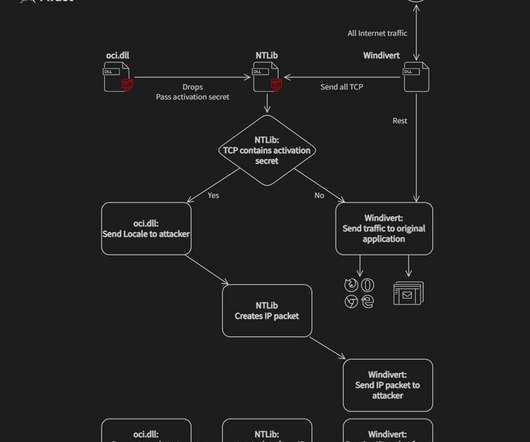
Citizen Lab published another report on the spyware used against two Egyptian nationals. One was hacked by NSO Group’s Pegasus spyware. The other was hacked both by Pegasus and by the spyware from another cyberweapons arms manufacturer: Cytrox. We haven’t heard a lot about Cytrox and its Predator spyware. According to Citzen Lab: We conducted Internet scanning for Predator spyware servers and found likely Predator customers in Armenia, Egypt, Greece, Indonesia, Madagascar, Oman, Saud






































Let's personalize your content