What’s Really the Reason Behind ‘The Great Resignation’?
Lohrman on Security
JANUARY 30, 2022
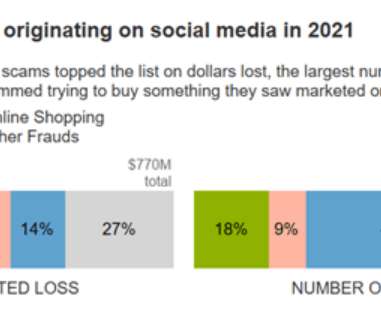
People changed jobs in record numbers in 2021, and 2022 is projected to bring more of the same. So what’s behind these trends? Let’s explore with the results of a new study from PlanBeyond.






























Let's personalize your content