Malicious Domain in SolarWinds Hack Turned into ‘Killswitch’
Krebs on Security
DECEMBER 16, 2020
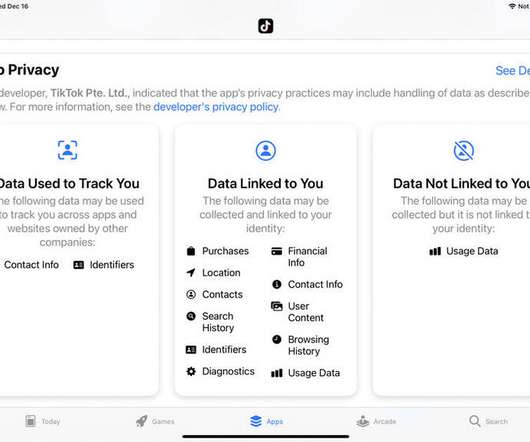
A key malicious domain name used to control potentially thousands of computer systems compromised via the months-long breach at network monitoring software vendor SolarWinds was commandeered by security experts and used as a “killswitch” designed to turn the sprawling cybercrime operation against itself, KrebsOnSecurity has learned. Austin, Texas-based SolarWinds disclosed this week that a compromise of its software update servers earlier this year may have resulted in malicious code





































Let's personalize your content