Why cybersecurity tools fail when it comes to ambiguity
Tech Republic Security
DECEMBER 25, 2020
Artificial intelligence will likely help with cybersecurity, though figuring out how to handle ambiguous situations is critical.

Tech Republic Security
DECEMBER 25, 2020
Artificial intelligence will likely help with cybersecurity, though figuring out how to handle ambiguous situations is critical.
Security Affairs
DECEMBER 25, 2020
Russian cryptocurrency exchange Livecoin was compromised on Christmas Eve, hackers breached its network and gained control of some of its servers. The Russian cryptocurrency exchange was hacked on Christmas Eve, it published a message on its website warning customers to stop using its services. “Dear clients, we ask you to stop using our service in all meanings: don’t deposit funds, don’t trade, don’t use API.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
DECEMBER 25, 2020
Creating an oasis of health in your home is getting easier with the help of sensors and IoT devices.
Security Affairs
DECEMBER 25, 2020
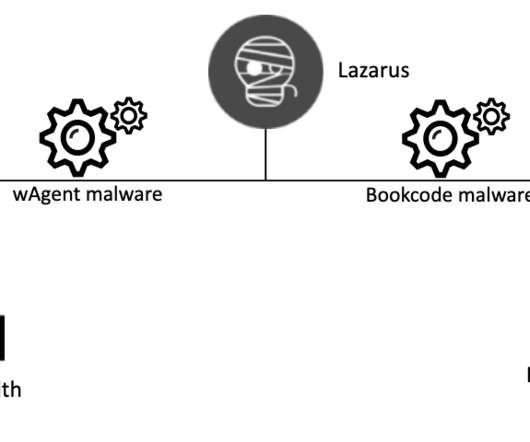
The North Korea-linked Lazarus APT group has recently launched cyberattacks against at least two organizations involved in COVID-19 research. The North Korea-linked APT group Lazarus has recently launched cyberattacks against two entities involved in COVID-19 research. The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

We Live Security
DECEMBER 25, 2020
Cyberthreats can take the fun out of connected gadgets – here's how to make sure your children enjoy the tech without putting themselves or their family at risk. The post Smart tech gifts: How to keep your kids and family safe appeared first on WeLiveSecurity.

Security Affairs
DECEMBER 25, 2020
CrowdStrike released a free Azure security tool after it was notified by Microsoft of a failed attack leveraging compromised Azure credentials. While investigating the impact of the recent SolarWind hack, on December 15th Microsoft reported to CrowdStrike that threat actors attempted to read CrowdStrike’s emails by using a compromised Microsoft Azure reseller’s account. “Specifically, they identified a reseller’s Microsoft Azure account used for managing CrowdStrike’s Microsoft
Let's personalize your content