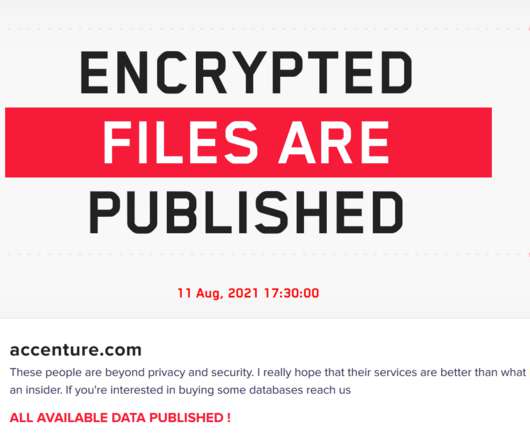
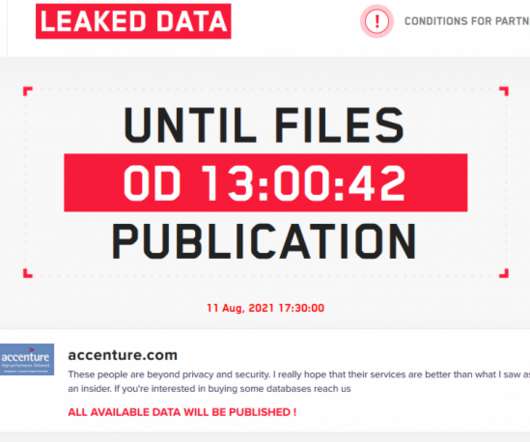
Cobolt Strike Vulnerability Affects Botnet Servers
Schneier on Security
AUGUST 11, 2021
Cobolt Strike is a security tool, used by penetration testers to simulate network attackers. But it’s also used by attackers — from criminals to governments — to automate their own attacks. Researchers have found a vulnerability in the product. The main components of the security tool are the Cobalt Strike client — also known as a Beacon — and the Cobalt Strike team server, which sends commands to infected computers and receives the data they exfiltrate.








































Let's personalize your content