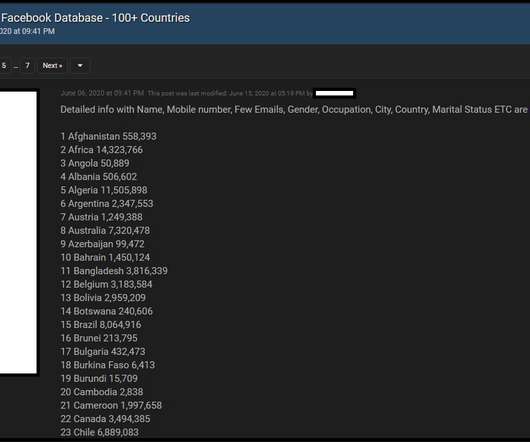
Microsoft outage caused by overloaded Azure DNS servers
Bleeping Computer
APRIL 3, 2021
Microsoft has revealed that Thursday's worldwide outage was caused by a code defect that allowed the Azure DNS service to become overwhelmed and not respond to DNS queries. [.].

























Let's personalize your content