On Trust and Transparency in Detection
Anton on Security
SEPTEMBER 14, 2022
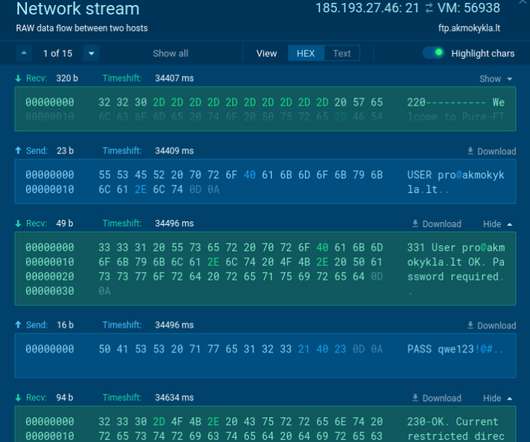
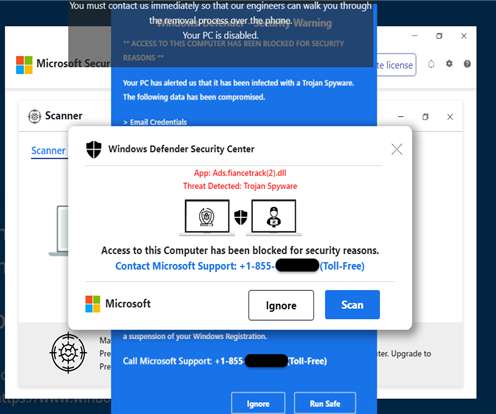
This blog / mini-paper is written jointly with Oliver Rochford. When we detect threats we expect to know what we are detecting. Sounds painfully obvious, right? But it is very clear to us that throughout the entire history of the security industry this has not always been the case. Some of us remember the early days of the network IDS intrusion detections systems were delivered without customers being able to see how the detections worked .





































Let's personalize your content