Cyberweapons Arms Manufacturer FinFisher Shuts Down
Schneier on Security
APRIL 6, 2022
FinFisher has shut down operations. This is the spyware company whose products were used, among other things, to spy on Turkish and Bahraini political opposition.

Schneier on Security
APRIL 6, 2022
FinFisher has shut down operations. This is the spyware company whose products were used, among other things, to spy on Turkish and Bahraini political opposition.

Tech Republic Security
APRIL 6, 2022
The Washington Post has revealed details of a contract with a software company that will allow the FBI to track social media posts. The post FBI investing millions in software to monitor social media platforms appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
APRIL 6, 2022
Digital transformation advances all business areas, fundamentally optimizing business processes and delivering value to customers. Successful digital transformation demands speed and agility over a sustained period, necessitating that cybersecurity keeps pace and becomes equally robust and responsive to changes in business and technology. Spending on digital transformation is expected to reach $1.8 trillion in 2022.

Tech Republic Security
APRIL 6, 2022
The scam was able to bypass Google and Microsoft’s email security filters after appearing to come from a legitimate email domain. The post Hackers employ voicemail phishing attacks on WhatsApp users appeared first on TechRepublic.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Bleeping Computer
APRIL 6, 2022
American cybersecurity company Palo Alto Networks warned customers on Wednesday that some of its firewall, VPN, and XDR products are vulnerable to a high severity OpenSSL infinite loop bug disclosed three weeks ago [.].

We Live Security
APRIL 6, 2022
ESET researchers analyzed three malicious applications targeting customers of eight Malaysian banks. The post Fake e‑shops on the prowl for banking credentials using Android malware appeared first on WeLiveSecurity.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Identity IQ
APRIL 6, 2022
Common Tech Support Scams and How to Avoid Them. IdentityIQ. These days, we live our lives online. Whether we’re ordering groceries or looking for new shoes, all we need to do is create an account, fill out some basic personal details and log in. But what happens when that account is compromised – or when we think that account is compromised? Maybe you get an email from technical support letting you know that your account has been breached and steps are needed to make it secure again.

Tech Republic Security
APRIL 6, 2022
Training may help alleviate some of these issues, along with clearer directives by management. The post Developers do not view application security as a top priority, study finds appeared first on TechRepublic.

CSO Magazine
APRIL 6, 2022
Since its inception in 2020, Zoom’s private bug bounty program has awarded $2.4 million in payments and swag to security researchers, recruiting over 800 ethical hackers via the HackerOne platform. In 2021 alone, it paid $1.8 million to researchers for helping to identify and resolve more than 400 security bugs, with its bounties now ranging from $250 up to $50,000.
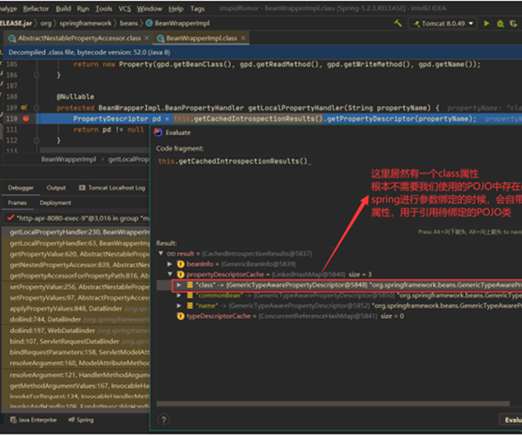
eSecurity Planet
APRIL 6, 2022
Spring4Shell ( CVE-2022-22965 ) is a remote code execution (RCE) vulnerability that affects Spring Core, a comprehensive framework for Java-based enterprise applications. Spring4Shell gets its name from the Log4Shell vulnerability , one of the most critical zero-day threats ever, which affected a Java software component called Log4j and allowed hackers to take control of web servers and networks.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Threatpost
APRIL 6, 2022
Threat actors target Office 365 and Google Workspace in a new campaign, which uses a legitimate domain associated with a road-safety center in Moscow to send messages.

Malwarebytes
APRIL 6, 2022
Unfortunately scammers continue to focus on the invasion of Ukraine to make money. A flurry of bogus domains and scam techniques are spreading their wings. They appear to focus on donation fakeouts but there’s a few other nasty surprises lying in wait too. The lowest of the low. There are few lower tactics than fake fundraising during times of crisis.

Security Affairs
APRIL 6, 2022
Nordex Group, one of the largest manufacturers of wind turbines, was hit by a cyberattack that forced the company to shut down part of its infrastructure. Nordex Group, one of the world’s largest manufacturers of wind turbines, was the victim of a cyberattack that forced the company to take down multiple systems. The attack was uncovered on March 31 and the company immediately started its incident response procedure to contain the attack.

CyberSecurity Insiders
APRIL 6, 2022
All Apple iPhone and iPAD users are issued a warning about a critical zero day vulnerability that has to be fixed on an immediate note. The technology company has issued a fix to the vulnerability that not only quashes the flaw but also protects device users from poor battery life. So, it is better if all iPhone and iPAD users navigate to the General tab> software updates and download and install the latest version of operating system, i.e. iOS 15.4.1.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Affairs
APRIL 6, 2022
Block disclosed a data breach related to the Cash App investing app and is notifying 8.2 million current and former US customers. The data breach involved a former employee that downloaded some unspecified reports of its Cash App Investing app that contained some U.S. customer information. Cash App is an app that allows users to easily send money, spend money, save money, and buy cryptocurrency. “On April 4, 2022, Block, Inc.

Cisco Security
APRIL 6, 2022
Security has never been more top of mind. Perhaps it’s exacerbated by what’s going on in Ukraine and the challenges it presents to the world, including the real fears over cyberwarfare. Of course, threats becoming advanced, the move to the cloud, and hybrid work remain among our customers’ biggest challenges. Who knew that when we all left the office more than two years ago, we would be gone to for so long—let alone hybrid work and its permanence becoming part of our work-life reality?

Bleeping Computer
APRIL 6, 2022
Microsoft has reminded customers that multiple.NET Framework versions signed using the insecure Secure Hash Algorithm 1 (SHA-1) will reach their end of life this month. [.].

Hacker Combat
APRIL 6, 2022
Ransomware attacks targeting governments, businesses, hospitals, and private individuals are rising. It has become a vast online issue that affects individuals and businesses alike. You are neither safe on your private nor public network, as ransomware can encrypt your files and hold them hostage. As a result, you have to pay ransom to unlock them. With so many businesses affected, there needs to be some way to combat this attack.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

CSO Magazine
APRIL 6, 2022
Malware authors are keeping with the times and when it comes to server-oriented malware. Specifically, attackers will adopt the same technologies their target organizations are using. Security researchers have recently come across a cryptocurrency miner that was designed to run inside AWS Lambda, a so-called serverless computing platform designed to execute user-supplied application code on demand.

Bleeping Computer
APRIL 6, 2022
An ongoing outage affects numerous Atlassian customers, causing their Jira and Confluence instances to not be accessible for over twenty-four hours. [.].

Security Affairs
APRIL 6, 2022
The U.S. Treasury Department sanctioned the Hydra Market, the world’s largest and longest-running dark web marketplace. The U.S. Treasury Department sanctioned the darkweb marketplace Hydra Market, the same day Germany’s Federal Criminal Police Office, the Bundeskriminalamt (BKA), announced they have shut down the illegal platform. The seizure of the Hydra Market is the result of an international investigation conducted by the Central Office for Combating Cybercrime (ZIT) in partnership wi

Bleeping Computer
APRIL 6, 2022
A new information stealer named FFDroider has emerged, stealing credentials and cookies stored in browsers to hijack victims' social media accounts. [.].

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Boulevard
APRIL 6, 2022
With rapidly increasing people's trust in online portals, offline services are changing the way, how many organizations work towards achieving their goals. For developing an authentic digital business solution, finding a perfect technology partner is a first and most crucial step. After this step only, your enterprise can look forward to establishing its brand [.].

Bleeping Computer
APRIL 6, 2022
VMware has warned customers to immediately patch critical vulnerabilities in multiple products that could be used by threat actors to launch remote code execution attacks. [.].

Security Affairs
APRIL 6, 2022
Ukraine’s technical security and intelligence service warns of threat actors targeting aimed at gaining access to users’ Telegram accounts. State Service of Special Communication and Information Protection (SSSCIP) of Ukraine spotted a new wave of cyber attacks aimed at gaining access to users’ Telegram accounts. The Ukrainian CERT attributes the hacking campaign to threat actors tracked as UAC-0094.

Heimadal Security
APRIL 6, 2022
Hydra Market, one of the largest dark web marketplaces in the world, has been shut down by the US Department of Justice (DOJ). Hydra’s servers and cryptocurrency wallets holding $25 million in bitcoin were captured by the DOJ and German federal police yesterday. What Is Hydra? Hydra was a popular Russian darknet marketplace with a […]. The post Russian Darknet Marketplace Hydra Shutdown by The US DOJ appeared first on Heimdal Security Blog.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

CSO Magazine
APRIL 6, 2022
Several years ago, we invited board members to speak candidly about presentations from company executives. Those free-flowing conversations more than lived up to what was billed as a “Don’t Bore the Board” panel discussion. The panel members’ engaging insights remain instructive to CISO s today as security leaders strive to hone their increasingly important board presentation approaches.

Bleeping Computer
APRIL 6, 2022
US government officials announced today the disruption of the Cyclops Blink botnet controlled by the Russian-backed Sandworm hacking group before being used in attacks. [.].

Security Boulevard
APRIL 6, 2022
It’s critical to find an effective way to prevent client-side web application attacks without overloading cybersecurity analysts. Here’s how. The post Addressing Material 3rd Party Risk Without Adding to Cybersecurity Analyst Burnout appeared first on Source Defense. The post Addressing Material 3rd Party Risk Without Adding to Cybersecurity Analyst Burnout appeared first on Security Boulevard.

Bleeping Computer
APRIL 6, 2022
British retail chain The Works announced it was forced to shut down several stores due to till issues caused by a cyber-security incident involving unauthorized access to its computer systems. [.].

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content