T-Mobile Investigating Claims of Massive Data Breach
Krebs on Security
AUGUST 16, 2021
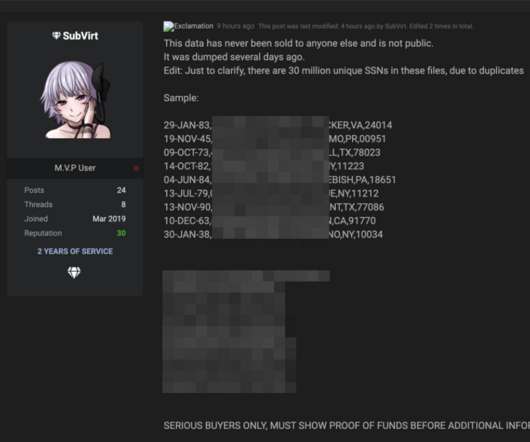
Communications giant T-Mobile said today it is investigating the extent of a breach that hackers claim has exposed sensitive personal data on 100 million T-Mobile USA customers, in many cases including the name, Social Security number, address, date of birth, phone number, security PINs and details that uniquely identify each customer’s mobile device.








































Let's personalize your content