Not All MFA is Equal, and the Differences Matter a Lot
Daniel Miessler
MARCH 10, 2022
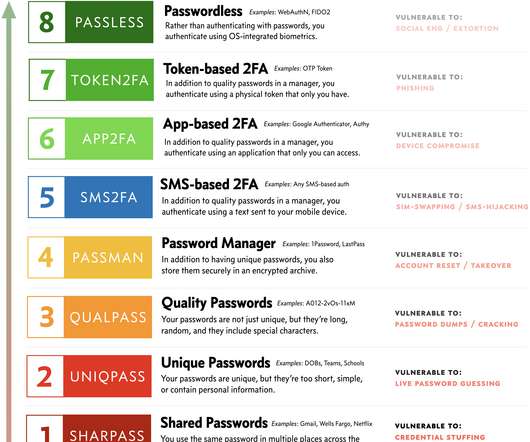
People are starting to get the fact that texts (SMS) are a weak form of multi-factor authentication (MFA). Fewer people know that there’s a big gap between the post-SMS MFA options as well. As I talked about in the original CASSM post , there are levels to this game. In that post we talked about 8 levels of password security, starting from using shared and weak passwords and going all the way up to passwordless.







































Let's personalize your content