QR Code Scam
Schneier on Security
DECEMBER 28, 2022
An enterprising individual made fake parking tickets with a QR code for easy payment.

Schneier on Security
DECEMBER 28, 2022
An enterprising individual made fake parking tickets with a QR code for easy payment.
Tech Republic Security
DECEMBER 28, 2022
A password manager can keep your sensitive information in-house. Here's how to deploy Passbolt to your data center or cloud-hosted service. The post How to deploy a self-hosted instance of the Passbolt password manager appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
DECEMBER 28, 2022
The Lake Charles Memorial Health System (LCMHS) is sending out notices of a data breach affecting thousands of people who have received care at one of its medical centers. [.].

CyberSecurity Insiders
DECEMBER 28, 2022
Smart Phones have become a need for us these days as they assist us in commuting, help in entertaining us if/when bored, help communicate with near & dear, read news and do more such stuff. But as these gadgets have turned crucial in our lives, many hackers are also interested in infiltrating them, to get our glimpse of our lives or where we are heading. .

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Bleeping Computer
DECEMBER 28, 2022
Malware operators have been increasingly abusing the Google Ads platform to spread malware to unsuspecting users searching for popular software products. [.].
Security Boulevard
DECEMBER 28, 2022
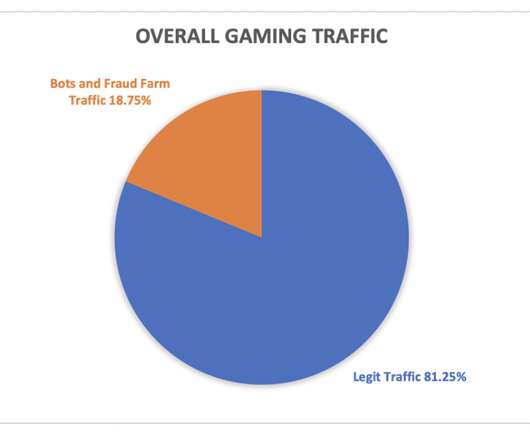
As the holiday season ramps up, online gamers spend more time in their favorite virtual worlds. From Nintendo to Xbox to “God of War” and “Call of Duty,” a flood of video games appear on the scene, encouraging players to invest even more time and money in this form of competitive entertainment. There are an […]. The post Gaming Companies Take Big Risks This Holiday appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Boulevard
DECEMBER 28, 2022
The world is full of machines and gadgets, readily participating in the race to automation, though, this race incorporates a hoard of convolutions. Albeit, IoT is the escape route to push these convolutions at bay, so IoT security plays a prime role. The interconnecting machines’ network that supports effortless data exchange is popularly termed IoT […].

CSO Magazine
DECEMBER 28, 2022
The Log4Shell critical vulnerability that impacted millions of enterprise applications remains a common cause for security breaches a year after it received patches and widespread attention and is expected to remain a popular target for some time to come. Its long-lasting impact highlights the major risks posed by flaws in transitive software dependencies and the need for enterprises to urgently adopt software composition analysis and secure supply chain management practices Log4Shell , official
Security Boulevard
DECEMBER 28, 2022
4 Reasons Why Security and Compliance Are Critical for Operational Resilience . Managing cybersecurity and compliance is always challenging, but it was even more so post-pandemic. As threat actors took advantage of changing business environments such as more remote teams and rapid technology adoption, cyber and compliance moved front and center. .

CyberSecurity Insiders
DECEMBER 28, 2022
Most of you connected to the world of data are in a misconception that both the terms data privacy and data security are same and are just the synonyms. But that’s not correct and here’s an explanation: Data Privacy is the word used to the practice of handling the data like how it is being collected, stored, used and whether it is covered under any compliance.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Bleeping Computer
DECEMBER 28, 2022
Thousands of Citrix ADC and Gateway deployments remain vulnerable to two critical-severity security issues that the vendor fixed in recent months. [.].

CyberSecurity Insiders
DECEMBER 28, 2022
For the first time, the hackers group that is being sponsored by North Korea State government is found spreading ransomware on computer networks related to companies and organizations operating in South Korea. According to the intelligence gathered by the National Police Agency of South Korea, the Kim Jong UN funded hacking groups were caught stealing email and identity related credentials related to over 890 foreign policy proficients in the past few weeks.

Security Boulevard
DECEMBER 28, 2022
Here are 4 cybersecurity trends for 2023 as IT teams and stakeholders turn their attention to implementing defensive strategies. The post Four Cybersecurity Predictions for 2023 appeared first on Enzoic. The post Four Cybersecurity Predictions for 2023 appeared first on Security Boulevard.

Heimadal Security
DECEMBER 28, 2022
The world’s largest cryptocurrency mining pool, BTC.com, announced it was the victim of a cyberattack that resulted in the theft of approximately $3 million worth of crypto assets. BTC.com is the seventh largest cryptocurrency mining pool, accounting for 2.66% of the network’s total hash rate, according to its mining pool tracker. Some Stolen Assets Recovered […].

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
DECEMBER 28, 2022
2022 was the year of the rise of the SBOM. This time of year, we take a look back at the havoc wreaked by breaches–that occurred in 2021 and earlier. The fallout from SolarWinds and Kaseya cyberattacks continued into 2022, which poignantly illustrated how vulnerable the software supply chain is. The Log4j open-source vulnerability at. 2022 was the year of the SBOM…and 2023 will be, too .

Dark Reading
DECEMBER 28, 2022
Will the bottom falling out of the cryptocurrency market have a profound impact on cybercriminal tactics and business models? Experts weigh in on what to expect.

The Hacker News
DECEMBER 28, 2022
Decentralized multi-chain crypto wallet BitKeep on Wednesday confirmed a cyberattack that allowed threat actors to distribute fraudulent versions of its Android app with the goal of stealing users' digital currencies.
WIRED Threat Level
DECEMBER 28, 2022
The password manager's most recent data breach is so concerning, users need to take immediate steps to protect themselves.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
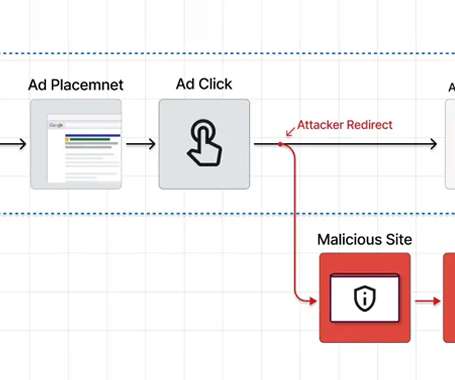
The Hacker News
DECEMBER 28, 2022
Users searching for popular software are being targeted by a new malvertising campaign that abuses Google Ads to serve trojanized variants that deploy malware, such as Raccoon Stealer and Vidar.
Security Affairs
DECEMBER 28, 2022
The chief executive of insurance giant Zurich warns that cyber attacks, rather than natural catastrophes, will become uninsurable. Mario Greco, chief executive of insurer giant Zurich, has warned that cyber attacks will become soon “uninsurable.”. The attacks are becoming even more frequent and the damage they are causing continues to grow. “What will become uninsurable is going to be cyber,” Mario Greco told the Financial Times.
Dark Reading
DECEMBER 28, 2022
According to the FBI and Internet Crime Complaint Center, 25% of ransomware complaints involve healthcare providers.

Security Affairs
DECEMBER 28, 2022
Decentralized multi-chain crypto wallet BitKeep lost over $9 Million worth of digital currencies after a cyber attack. BitKeep was the victim of a supply chain attack that resulted in the theft of over $9 Million worth of digital currencies from its customers. The attack took place on December 26, threat actors were able to distribute tainted versions of the company’s Android app that were designed to steal users’ digital assets.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Heimadal Security
DECEMBER 28, 2022
The Federal Bureau of Investigation (FBI) issued an alert about cyber criminals using a new methodology to defraud users – brand impersonation via search engine advertisement services. The victims are led to malicious websites that host ransomware and steal login credentials and other financial information. At first, cyber criminals buy advertisements that appear in internet […].

Security Boulevard
DECEMBER 28, 2022
As the year is coming to an end, I can’t help but take a walk down memory lane to reminisce and reflect on the journey of the cloud threat landscape. Here’s my take on this 2022 recap of cloud threats. First things first, I think it’s safe to say that this year has been a rollercoaster of non-stop cyberattacks. Particularly the cloud threat landscape, it truly feels like the massive potholes in front of my home.

Dark Reading
DECEMBER 28, 2022
This is what happens when a CISO gets tired of reacting to attacks and goes on the offensive.

Bleeping Computer
DECEMBER 28, 2022
The Royal Ransomware gang claimed responsibility for a cyber attack against telecommunications company Intrado on Tuesday. [.].

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Naked Security
DECEMBER 28, 2022
If the crooks have connected up your phone number and your Twitter handle. what could go wrong?

Security Boulevard
DECEMBER 28, 2022
stackArmor’s ThreatAlert® ATO Accelerator helps ISVs and SaaS providers reduce the time and cost of FedRAMP authorizations December 21, 2022 14:16 ET | Source: stackArmor, Inc. TYSONS CORNER, Va., Dec. 21, 2022 (GLOBE NEWSWIRE) — stackArmor, Inc., a leading provider of Federal Risk and Authorization Management Program (FedRAMP®), Federal Information Security Modernization Act (FISMA), CMMC […].

WIRED Threat Level
DECEMBER 28, 2022
The Kremlin’s aggression in Ukraine is following a dangerous playbook that began to unfold years ago.

Security Boulevard
DECEMBER 28, 2022
PINEHURST, NORTH CAROLINA, USA, December 22, 2022 /EINPresswire.com/ — TERIDA, the award-winning, women-owned-controlled-led, RegTech small business, today, announced the next stage of their Federal Risk and Authorization Management Program (FedRAMP®) journey – ‘FedRAMP In Process’ designation for their cloud platform, the Terida RegTech Framework – CLASsoft™.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content