The Subsequent Waves of log4j Vulnerabilities Aren’t as Bad as People Think
Daniel Miessler
DECEMBER 18, 2021
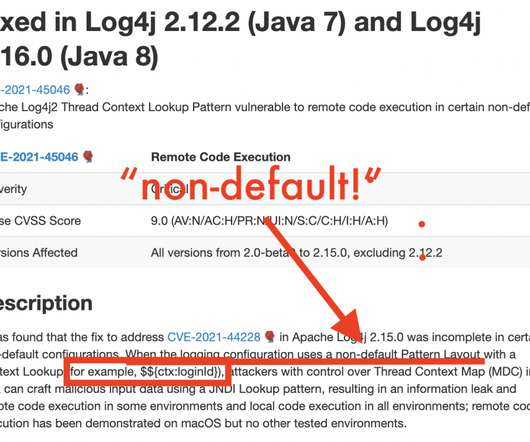
If you’re reading this you’re underslept and over-caffeinated due to log4j. Thank you for your service. I have some good news. I know a super-smart guy named d0nut who figured something out like 3 days ago that very few people know. Once you have 2.15 applied—or the CLI implementation to disable lookups—you actually need a non-default log4j2.properties configuration to still be vulnerable!



























Let's personalize your content