CyberWar In Ukraine: A 21st Century Epilogue To The Cold War (InfoGraphic)
Joseph Steinberg
DECEMBER 6, 2022
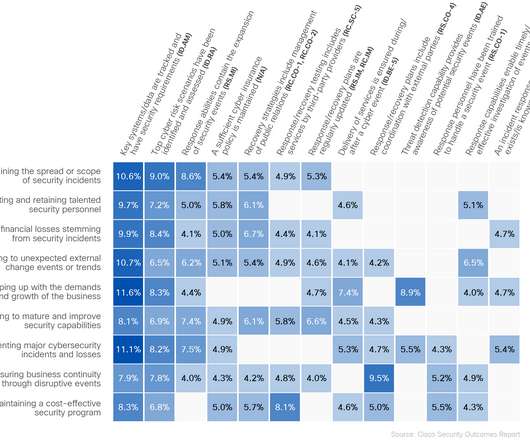
The era of cyberwar has not only arrived, but is advancing rapidly – and the repercussions of the march forward are nothing short of terrifying. The following infographic, reproduced with permission from Nowsourcing, highlights how Ukraine has become the battleground between Russia and the United States, in a 21st Century epilogue to the Cold War: This infographic originally appeared here , and is reproduced with permission.









































Let's personalize your content