Zoom Exploit on MacOS
Schneier on Security
AUGUST 17, 2022
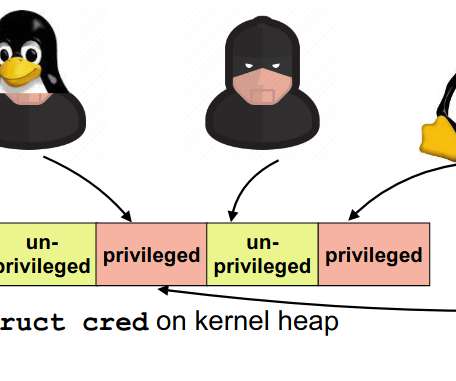
This vulnerability was reported to Zoom last December: The exploit works by targeting the installer for the Zoom application, which needs to run with special user permissions in order to install or remove the main Zoom application from a computer. Though the installer requires a user to enter their password on first adding the application to the system, Wardle found that an auto-update function then continually ran in the background with superuser privileges.








































Let's personalize your content