Microsoft Office 365 still the top target among phishing attacks
Tech Republic Security
MARCH 31, 2021
Most of the recent credential phishing attacks seen by Menlo Security served phony Outlook and Office 365 login pages.

Tech Republic Security
MARCH 31, 2021
Most of the recent credential phishing attacks seen by Menlo Security served phony Outlook and Office 365 login pages.

The Last Watchdog
MARCH 31, 2021
The start of 2021 brings forth a cyber security crossroads. Many people are in the process of shifting back into office operations while balancing the potential risks and benefits of remote work. Related: Breaches spike during pandemic. For some malicious hackers and IT experts, this could represent an opening. From the known compromise vectors to the most recent threats, hackers are constantly on the lookout for new strategies to bypass IT notice, out maneuver defense setups, and take advantage
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
MARCH 31, 2021
Malware is being hidden in seemingly legitimate files that gamers download to install cheat codes or modifications, says Cisco Talos.

We Live Security
MARCH 31, 2021
From losing cherished memories to missing deadlines, the impact of not having backups when a data disaster strikes can hardly be overstated. The post Are you prepared to prevent data loss? appeared first on WeLiveSecurity.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.
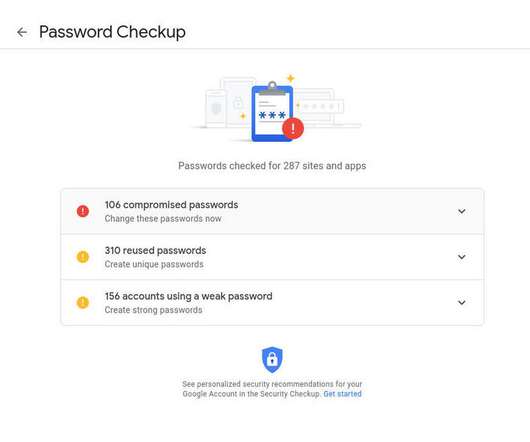
Tech Republic Security
MARCH 31, 2021
Google offers a password checking service that will check all of your Chrome-saved passwords for weaknesses and against known breaches. Jack Wallen shows you how to use this tool.
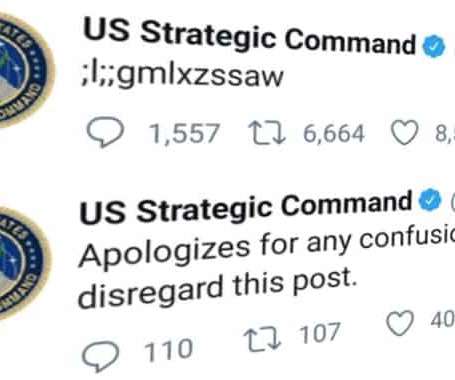
Graham Cluley
MARCH 31, 2021
When an unintelligible tweet was made by the US Strategic Command's Twitter account, it's understandable that some folks might imagine a password was accidentally published to the world, or that perhaps the account had been compromised, or. gulp! that it might be a US nuclear launch code.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

CyberSecurity Insiders
MARCH 31, 2021
This article originally appeared in a global white paper examining the issues around vaccination certificates and immunity passports, and released by Reconnaissance International during the Digital Documents Security virtual event. As vaccination programmes gather momentum, attention is turning towards restoring individual freedoms and reviving economies.
Bleeping Computer
MARCH 31, 2021
Distributed denial-of-service (DDoS) attacks started strong this year, setting new records and taking the extortion trend that started last August to the next level. [.].

Tech Republic Security
MARCH 31, 2021
Technology shows us once that tech build for good people can be harnessed by bad actors. Experts talk about how criminals are operating, and what you can do about it.

Security Boulevard
MARCH 31, 2021
A security professional who assisted Ubiquiti in its response to a data breach accused the Internet-of-Things (IoT) device vendor of having downplayed the incident’s severity. The post Whistleblower Accuses Ubiquiti of Downplaying Major Data Breach appeared first on Security Boulevard.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
MARCH 31, 2021
Employees are increasingly using their own devices and accounts to work from home - largely because it's easier to do so. Yet this rise in 'shadow IT' puts corporate security at risk.

Security Boulevard
MARCH 31, 2021
. A roundup of UK focused Cyber and Information Security News, Blog Posts, Reports and general Threat Intelligence from the previous calendar month, March 2021. How not to disclosure a Hack. UK fashion retailer FatFace angered customers in its handling of a customer data theft hack. The clothes retailer revealed a data theft which included its customer's full names, home addresses, email addresses, and partial debitcredit card details.

Bleeping Computer
MARCH 31, 2021
Threat actors target gamers with backdoored game tweaks, patches, and cheats hiding malware capable of stealing information from infected systems. [.].

SecureList
MARCH 31, 2021
2020 was challenging for everyone: companies, regulators, individuals. Due to the limitations imposed by the epidemiological situation, particular categories of users and businesses were increasingly targeted by cybercriminals. While we were adjusting to remote work and the rest of the new conditions, so were scammers. As a result, 2020 was extremely eventful in terms of digital threats, in particular those faced by financial institutions.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
TrustArc
MARCH 31, 2021
During the “A New Era of Privacy: Perspectives from Privacy Practitioners” roundtable at the recent TrustArc Privacy Risk Summit, experts explored the privacy challenges presented during 2020, trends in privacy and risk management and the role technology can play in addressing these hurdles. The wide-ranging conversation clearly highlighted the growing need for comprehensive and intuitive […].

Bleeping Computer
MARCH 31, 2021
Google Chrome developers have announced plans to roll out DNS-over-HTTPS (DoH) support to Chrome web browser for Linux. DoH has been supported on Google Chrome for other platforms, including Android, since at least 2020. But, there's a catch. [.].

Security Boulevard
MARCH 31, 2021
Amid the pandemic, most workforces have shifted to remote work and home offices; essentially, transforming their living rooms into corporate branch offices. From a convenience and health perspective, this has worked well, for the most part. However, the convenience of working from home has put a lot of responsibility on corporate IT folks to ensure.

Tech Republic Security
MARCH 31, 2021
The IRS is warning of a phishing scam that promises refund information but looks to capture Social Security numbers and other sensitive data.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

SC Magazine
MARCH 31, 2021
Centripetal Networks filed a lawsuit this month accusing Palo Alto of violating 12 separate patents for systems or policies designed to enhance network security. Seen here, an aerial view of Palo Alto’s Santa Clara campus. (Palo Alto). A company is suing Palo Alto Networks patent infringement, alleging that their proprietary technologies were used in a number of major security products and systems sold by the cybersecurity giant.

Hot for Security
MARCH 31, 2021
The US Department of Justice (DoJ) has charged nearly 500 individuals for allegedly participating in coronavirus-related scams and fraudulent activities. As of March 26, 474 individuals have been publicly charged with COVID-19 fraud schemes focused on siphoning over $569 million from government financial relief projects, including the Paycheck Protection Program (PPP), Economic Injury Disaster Loan (EIDL) program and Unemployment Insurance (UI) programs.

Tech Republic Security
MARCH 31, 2021
Cincinnati Reds fans: It's especially time for you to rethink your team as a common part of your credentials.

Threatpost
MARCH 31, 2021
Telecommuting social-media manager for the U.S. Strategic Command left the laptop open and unsecured while stepping away.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Boulevard
MARCH 31, 2021
Two mega-breaches caused by third parties have occurred over the last month, adding to the recent Solarwinds epic supply chain hack, to create a growing tsunami of third party risk for enterprises and government organizations. Security software provider Accellion suffered a breach in their FTA tool which caused many of their clients to have their […].

Tech Republic Security
MARCH 31, 2021
Adopting a hybrid approach can help organizations run, unify and secure all digital identities in an IT architecture, new research finds.

CyberSecurity Insiders
MARCH 31, 2021
In the past couple of weeks, most of the populace living in the suburbs of London is complaining of a cyber fraud in which all their earnings were drained out by a Royal Mail text that had a malicious link. What’s interesting about the scam is that even the law enforcement cannot intervene in the issue to get refunds back from the bank. Cybersecurity Insiders has learnt that millions of people across UK have received a message that is leading to a money draining fraud with an estimate of victims

Bleeping Computer
MARCH 31, 2021
For the past two months, security researchers have been waging an online battle against a new 'BazarCall' malware that uses call centers to distribute some of the most damaging Windows malware. [.].

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Boulevard
MARCH 31, 2021
The fundamentals of a formal, effective application security plan should start with business objectives, tools, processes and most of all, data, with the primary driver for securing applications focused on protecting data. While it is important to surgically address the insecurities in a mission-critical application, it is equally important to continuously upskill the development and.

CyberSecurity Insiders
MARCH 31, 2021
Ziggy Ransomware gang has decided to do good to the society by offering a refund to all its victims. Why they are doing so or their motive behind this act of kindness is yet to be known. But those spreading the said file encrypting malware have taken a pledge on Telegram to refund back the money extracted from their victims as ransom through. . Therefore, the refund campaign that started in February this year is said to benefit over 300 victims and additionally the threat actors have also chosen

Cisco Security
MARCH 31, 2021
For the first time ever, Cisco is bringing customers and partners from all around the world together for an all-in-one global event! This week, we are delivering an experience unlike any other; this comes at an interesting time for Cisco SecureX. SecureX has been simplifying security for almost an entire year now and it has defined what a true security platform approach means by giving security and IT decision makers a more effective way to protect and interact with their growing networks.

Graham Cluley
MARCH 31, 2021
Graham Cluley Security News is sponsored this week by the folks at Recorded Future. Thanks to the great team there for their support! Recorded Future provides deep, detailed insight into emerging threats by automatically collecting, analyzing, and organizing billions of data points from the Web. And now, with its FREE Cyber Daily email all IT … Continue reading "Get FREE threat intelligence on hackers and exploits with the Recorded Future Cyber Daily".

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content