At Least 30,000 U.S. Organizations Newly Hacked Via Holes in Microsoft’s Email Software
Krebs on Security
MARCH 5, 2021
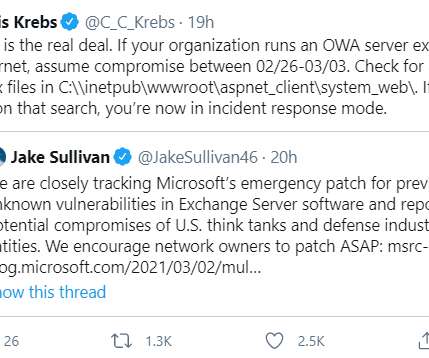
At least 30,000 organizations across the United States — including a significant number of small businesses, towns, cities and local governments — have over the past few days been hacked by an unusually aggressive Chinese cyber espionage unit that’s focused on stealing email from victim organizations, multiple sources tell KrebsOnSecurity.




































Let's personalize your content