Privacy Analysis of Ambient Light Sensors
Schneier on Security
SEPTEMBER 15, 2020
Interesting privacy analysis of the Ambient Light Sensor API. And a blog post. Especially note the “Lessons Learned” section.
Schneier on Security
SEPTEMBER 15, 2020
Interesting privacy analysis of the Ambient Light Sensor API. And a blog post. Especially note the “Lessons Learned” section.
Tech Republic Security
SEPTEMBER 15, 2020
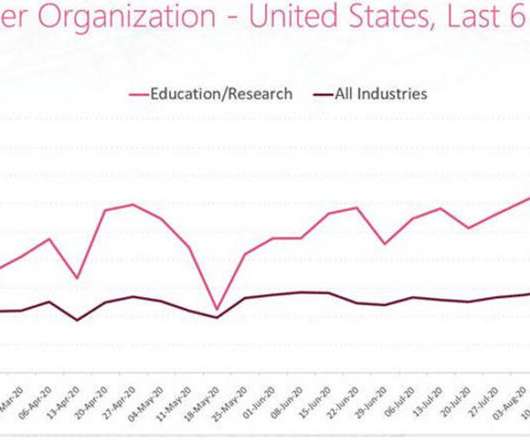
With the back-to-school season, schools and academic organizations are seeing an increase in cyberattacks, says Check Point Research.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Schneier on Security
SEPTEMBER 15, 2020
This is a current list of where and when I am scheduled to speak: I’m speaking at the Cybersecurity Law & Policy Scholars Virtual Conference on September 17, 2020. I’m keynoting the Canadian Internet Registration Authority’s online symposium, Canadians Connected , on Wednesday, September 23, 2020. I’m giving a webinar as part of the Online One Conference 2020 on September 29, 2020.
Tech Republic Security
SEPTEMBER 15, 2020
Jack Wallen shows you how to run a phishing simulation on your employees to test their understanding of how this type of attack works.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

WIRED Threat Level
SEPTEMBER 15, 2020
Sara-Jayne Terp uses the tools of cybersecurity to track false claims like they’re malware. Her goal: Stop dangerous lies from hacking our beliefs.

Tech Republic Security
SEPTEMBER 15, 2020
The world is too dangerous to use the internet unprotected. Save your computers, tablets, and phones from being attacked with these options.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
SEPTEMBER 15, 2020
CISOs are turning to automation to address concerns about doing more with less, preparing for audits remotely, and speeding evidence collection, according to a newly released study.

Threatpost
SEPTEMBER 15, 2020
Vulnerabilities ‘that have existed for years’ in WS-Trust could be exploited to attack other services such as Azure and Visual Studio.

Tech Republic Security
SEPTEMBER 15, 2020
Checking users, applications, and devices on your network are just a few ways to keep your company safe from cyberattacks. Tom Merritt lists five things to know about zero trust ops.

Security Affairs
SEPTEMBER 15, 2020
The British National Cyber Security Centre (NCSC) released a guideline, dubbed The Vulnerability Disclosure Toolkit, for the implementation of a vulnerability disclosure process. The UK National Cyber Security Centre (NCSC) has released a guideline, dubbed The Vulnerability Disclosure Toolkit, on how to implement a vulnerability disclosure process. The guidelines highlight the importance for any organization to encourage responsible bug reporting through specifically-defined processes.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
SEPTEMBER 15, 2020
Without early threat detection, you may not know your website has been hit by a DDoS attack until it slows down or stops, says NordVPN Teams.

WIRED Threat Level
SEPTEMBER 15, 2020
The US government has detained thousands of wireless earbuds on suspicion of being fake Apple goods—despite crystal clear branding from an established company.

Tech Republic Security
SEPTEMBER 15, 2020
Cybercriminals are increasingly exploiting the Cobalt Strike testing toolkit to carry out ransomware campaigns, says Cisco Talos Incident Response.

Security Affairs
SEPTEMBER 15, 2020
Microsoft released the Project OneFuzz, an open-source fuzzing framework for its cloud computing service Azure. Microsoft this week announced the release of the Project OneFuzz which is an open-source fuzzing framework for its cloud computing service Azure. The project was previously used by the IT giant to find vulnerabilities in the popular service. “Today, we’re excited to release this new tool called Project OneFuzz, an extensible fuzz testing framework for Azure.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Tech Republic Security
SEPTEMBER 15, 2020
Checking users, applications, and devices on your network are just a few ways to keep your company safe from cyberattacks. Tom Merritt lists five things to know about zero trust ops.

WIRED Threat Level
SEPTEMBER 15, 2020
How Dana DeBeauvoir set off the biggest, weirdest, and most promising revolution in election technology since the 1800s.
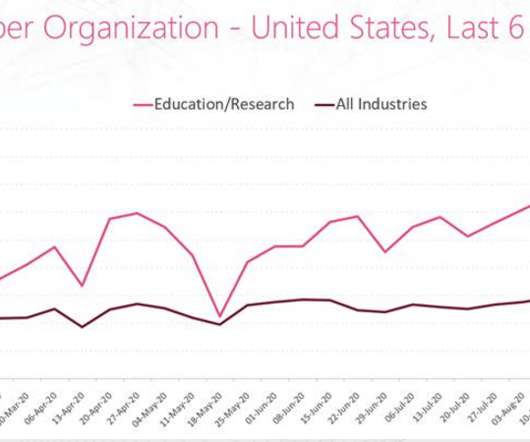
Security Affairs
SEPTEMBER 15, 2020
Experts warn of a surge in the DDoS attacks against education institutions and the academic industry across the world. While the popularity of online learning is increasing due to the ongoing Coronavirus pandemic, threat actors are launching distributed denial-of-service (DDoS) on education institutions and the academic industry across the world. The DDoS attacks are causing severe issues to the targeted education institutions such as temporarily takedown of the network and online classes.

Threatpost
SEPTEMBER 15, 2020
Two bugs (CVE-2020-4703 and CVE-2020-4711) in IBM's Spectrum Protect Plus data-storage protection solution could enable remote code execution.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Affairs
SEPTEMBER 15, 2020
Adobe has released an out-of-band security update to address three ‘Important’ security vulnerabilities in the Adobe Media Encoder. Adobe has released an out-of-band security update for Adobe Media Encoder that addresses three ‘Important’ Information Disclosure flaws. The three vulnerabilities could be exploited by an attacker to access sensitive information that is leaked in the security of the active user.
WIRED Threat Level
SEPTEMBER 15, 2020
The Kremlin has meddled in so many elections that democracy’s immune system has gotten wise to its threats. Here are lessons other countries can teach us.

Threatpost
SEPTEMBER 15, 2020
QR code usage is soaring in the pandemic -- but malicious versions aren't something that most people think about.

WIRED Threat Level
SEPTEMBER 15, 2020
Whether you’re casting a ballot in person or by mail, there’s plenty to worry about. Mass voter fraud shouldn’t be on the list.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Dark Reading
SEPTEMBER 15, 2020
The pandemic-related shift to remote work and the growing availability of ransomware-as-a-service were two major drivers, CrowdStrike says.

Threatpost
SEPTEMBER 15, 2020
Social engineering and employee mistakes lead to breach Veteran's Administration and the National Health Service.

NSTIC
SEPTEMBER 15, 2020
This post is part of a series on differential privacy. Learn more and browse all the posts published to date on the differential privacy blog series page in NIST’s Privacy Engineering Collaboration Space. It's not so simple to deploy a practical system that satisfies differential privacy. Our example in the last post was a simple Python program that adds Laplace noise to a function computed over the sensitive data.

Dark Reading
SEPTEMBER 15, 2020
Without the right reinforcements, you could be barking at the moon.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Affairs
SEPTEMBER 15, 2020
CISA published an advisory on China-linked groups targeting government agencies by exploiting flaws in Microsoft Exchange, Citrix, Pulse, and F5 systems. CISA published a security advisory warning of a wave of attacks carried out by China-linked APT groups affiliated with China’s Ministry of State Security. Chinese state-sponsored hackers have probed US government networks looking for vulnerable networking devices that could be compromised with exploits for recently disclosed vulnerabiliti

Dark Reading
SEPTEMBER 15, 2020
CISA has issued an alert following the discovery of publicly available exploit code for Windows elevation of privilege flaw CVE-2020-1472.

Veracode Security
SEPTEMBER 15, 2020
Sensitive data exposure is currently at number 3 in the??? OWASP Top 10 ???list of the most critical application security risks. In this blog post, we will describe common scenarios of incorrect sensitive data handling and suggest ways to protect sensitive data. We will illustrate our suggestions with code samples in C# that can be used in ASP.NET Core applications.

Dark Reading
SEPTEMBER 15, 2020
As many organizations pivot to working from home, here are some considerations for prioritizing the new security protocols.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content