LastPass releases new security incident disclosure and recommendations
Tech Republic Security
MARCH 4, 2023
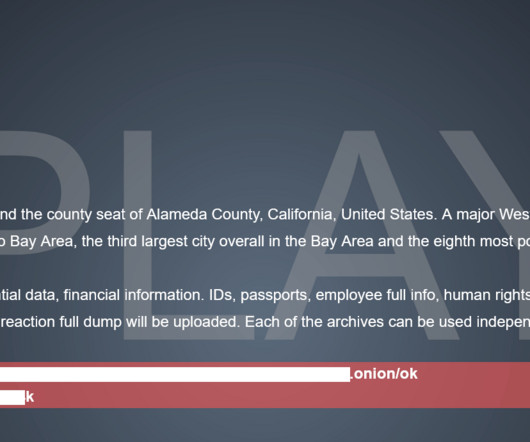
LastPass attacks began with a hacked employee's home computer. The investigation now reveals the password manager company's data vault was compromised. The post LastPass releases new security incident disclosure and recommendations appeared first on TechRepublic.























Let's personalize your content