The Road To ggplot2 In WebR, Part 1: The Road Is Paved With Good Base R Plots
Security Boulevard
MARCH 18, 2023
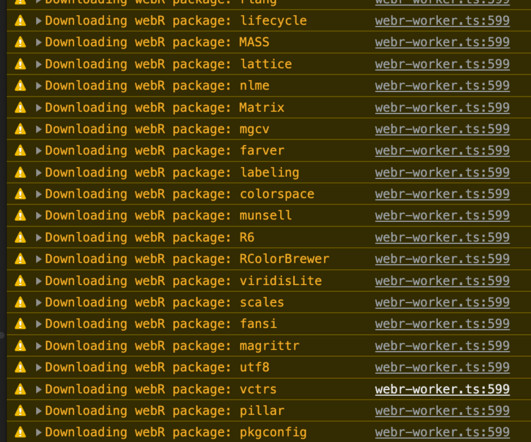
I have graphics working in Vanilla JS WebR, now, and I’ll cover the path to that in two parts. The intent was to jump straight into ggplot2-land, but, as you saw in my previous post, WASM’d ggplot2 is a bear. And, I really didn’t grok what the WebR site docs were saying about how to. Continue reading → The post The Road To ggplot2 In WebR, Part 1: The Road Is Paved With Good Base R Plots appeared first on Security Boulevard.
 52
52  52
52 



















Let's personalize your content