Check for Log4j vulnerabilities with this simple-to-use script
Tech Republic Security
DECEMBER 28, 2021
If you're not certain whether your Java project is free from Log4j vulnerabilities, you should try this easy-to-use scanning tool immediately.

Tech Republic Security
DECEMBER 28, 2021
If you're not certain whether your Java project is free from Log4j vulnerabilities, you should try this easy-to-use scanning tool immediately.

Bleeping Computer
DECEMBER 28, 2021
Many LastPass users report that their master passwords have been compromised after receiving email warnings that someone tried to use them to log into their accounts from unknown locations. [.].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
DECEMBER 28, 2021
The post Top DevOps Trends That Will Dominate in 2022 appeared first on PeoplActive. The post Top DevOps Trends That Will Dominate in 2022 appeared first on Security Boulevard.

Bleeping Computer
DECEMBER 28, 2021
Apache has released another Log4j version, 2.17.1 fixing a newly discovered remote code execution (RCE) vulnerability in 2.17.0, tracked as CVE-2021-44832. Prior to today, 2.17.0 was the most recent version of Log4j and deemed the safest release to upgrade to, but that advice has now evolved. [.].

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

CSO Magazine
DECEMBER 28, 2021
Many employees at businesses worldwide have been forced to work from home because of COVID-19 related social distancing mandates. The security of employee home networks, and of the devices connected to them, are becoming increasingly important considerations for organizations that need to continue to support a large remote workforce for the foreseeable future.

Bleeping Computer
DECEMBER 28, 2021
The RedLine information-stealing malware targets popular web browsers such as Chrome, Edge, and Opera, demonstrating why storing your passwords in browsers is a bad idea. [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
DECEMBER 28, 2021
An Amazon Echo owner was left shocked after Alexa proposed a dangerous challenge to her 10-year old child. AI-powered virtual assistants like Alexa that power smart devices and speakers such as Echo, Echo Dot, and Amazon Tap, come with a plethora of capabilities, including playing verbal games. [.].
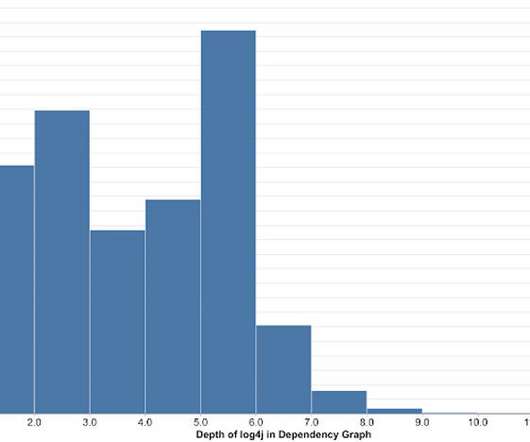
Dark Reading
DECEMBER 28, 2021
Over 80% of Java packages stored on Maven Central Repository have log4j as an indirect dependency, with most of them burying the vulnerable version five levels deep, says Google's Open Source Insights Team.

CSO Magazine
DECEMBER 28, 2021
I wrote previously of what the key ingredients are for a successful travel program might include, as it was a topic which had not garnered much attention over the course of the past couple of years as pandemic took hold. What most entities have experienced since early 2020 is the IT scramble to accommodate the migration by employees from onsite and in their seat, to off-site and sitting wherever they could find internet access.

CyberSecurity Insiders
DECEMBER 28, 2021
T Mobile that suffered a massive data breach in August this year has again fallen prey to a similar hack in December 2021 that saw information leak of a small set of the telecom company customers. According to those reporting to our Cybersecurity Insiders, the attack took place in three forms, with the first targeting the customer proprietary network info(cpni), and second related to SIM swap and third involving customers targeted with both the said forms of incidents.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Bleeping Computer
DECEMBER 28, 2021
The cyber-espionage APT (advanced persistent threat) group tracked as 'BlackTech' was spotted using a novel malware called 'Flagpro' in attacks against Japanese firms. [.].

CyberSecurity Insiders
DECEMBER 28, 2021
All those using cryptocurrency wallets, you better be aware of this crypto scam that is being spread through Telegram. Information is out that some hackers in the name of ‘Smokes Night’ are stealing cryptocurrency from the users’ wallets by spreading Echelon Malware on Telegram. Technically, Echelon is a malicious software that is into the tactic of stealing information of those using Telegram messaging services.

The Hacker News
DECEMBER 28, 2021
The Apache Software Foundation (ASF) on Tuesday rolled out fresh patches to contain an arbitrary code execution flaw in Log4j that could be abused by threat actors to run malicious code on affected systems, making it the fifth security shortcoming to be discovered in the tool in the span of a month. Tracked as CVE-2021-44832, the vulnerability is rated 6.

Security Boulevard
DECEMBER 28, 2021
This week brought news of Chinese hackers attacking Microsoft Exchange. But why did Microsoft wait eight weeks to tell anyone? The post Best of 2021 – Chinese Exchange Hack: At Best, Microsoft is Incompetent appeared first on Security Boulevard.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Threatpost
DECEMBER 28, 2021
Security flaws in the recently released Fisher-Price Chatter Bluetooth telephone can allow nearby attackers to spy on calls or communicate with children using the device.

CyberSecurity Insiders
DECEMBER 28, 2021
McMenamins, a family owned company of crafted breweries in Oregon & Washington, has reportedly suffered a ransomware attack, blocking down several of its digital services like hotel room booking and such. The employees of the company have been asked to use other digital services to stay in touch with each other and were given a hint that it might take at least 10 days for the business to recover from the incident.

Security Boulevard
DECEMBER 28, 2021
In this article, we’ll take a look back at the changes to the OWASP Top 10 this past year. Photo by Anna Tarazevich from Pexels. It’s been four years since OWASP updated its Top 10 list , but this year we got three brand new categories along with a reshuffling of the rest. As we head into 2022, we’ll take a look at the generalization of the guidance offered by OWASP, changes in how the team determined which issues were included/excluded, and how some things never change.
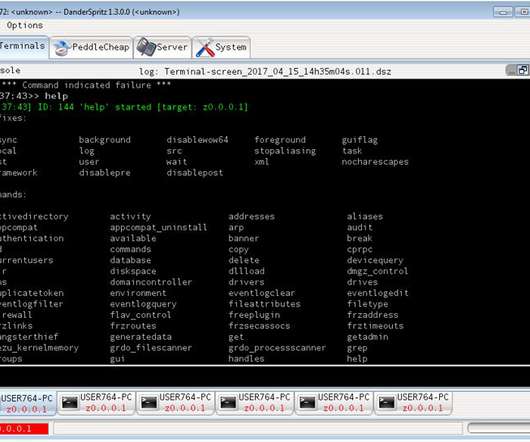
The Hacker News
DECEMBER 28, 2021
Cybersecurity researchers have offered a detailed glimpse into a system called DoubleFeature that's dedicated to logging the different stages of post-exploitation stemming from the deployment of DanderSpritz, a full-featured malware framework used by the Equation Group.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
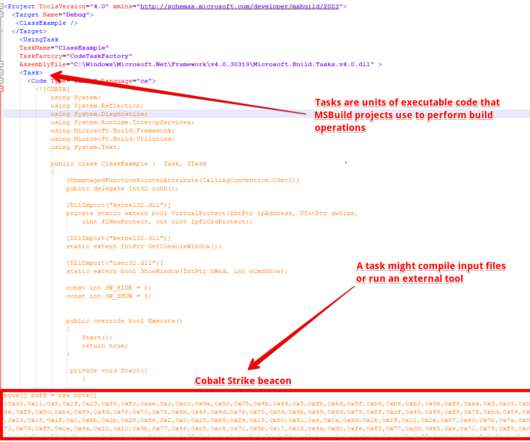
Security Affairs
DECEMBER 28, 2021
Experts warn of malicious campaigns abusing Microsoft Build Engine (MSBuild) to execute a Cobalt Strike payload on compromised systems. Security expert from Morphus Labs recently observed several malicious campaigns abusing Microsoft Build Engine ( MSBuild ) to execute a Cobalt Strike payload on compromised machines. MSBuild is a free and open-source build toolset for managed code as well as native C++ code and was part of.NET Framework.

Dark Reading
DECEMBER 28, 2021
Severe flaws in Microsoft Exchange and Windows Print Spooler stood out amid a wide range of vulnerabilities security teams were forced to prioritize in 2021.

Security Affairs
DECEMBER 28, 2021
Password manager app LastPass confirmed that threat actors have launched a credential stuffing attack against its users. While LastPass says that it is not aware that some of its accounts were compromised in the recent credential stuffing attacks that started on Monday, numerous LastPass users claim that their master passwords have been compromised after receiving emails warning them that someone tried to use them to access their accounts. “Someone just used your master password to try to

Security Boulevard
DECEMBER 28, 2021
The City of Keizer is a beautiful community in the Willamette Valley of Oregon. The city offers an ideal environment, delivering a range of services to citizens, from parks and public works to police protection. However, even from its earliest days, there have been hazards to overcome. As a settlement in the 1800s, floods forced the community to rebuild on.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Heimadal Security
DECEMBER 28, 2021
A jump in the number of eCh0raix ransomware attacks on the systems of QNAP NAS devices has been reported by users. The ransomware is also known under the name of QNAPCrypt. It seems that the cybercriminals behind eCh0raix started to increase their activity a week before the Christmas holidays. They are targeting devices with admin […]. The post An Increased Wave of eCh0raix Ransomware Attacks Hits QNAP NAS Devices appeared first on Heimdal Security Blog.

Security Boulevard
DECEMBER 28, 2021
The cybersecurity market offers excellent solutions and services to combat the threats that are exploited by cybercriminals. However, are these tools enough to fully protect an organization? It is clear that human error is a strong attack vector for many popular cybercrimes, so the best way to augment any security program is to create a cyber-aware workforce.

Bleeping Computer
DECEMBER 28, 2021
Samsung's official Android app store, called the Galaxy Store, has had an infiltration of riskware apps that triggered multiple Play Protect warnings on people's devices. [.].
Security Boulevard
DECEMBER 28, 2021
The post Top 10 Challenges of DevOps Adoption in 2022 appeared first on PeoplActive. The post Top 10 Challenges of DevOps Adoption in 2022 appeared first on Security Boulevard.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Appknox
DECEMBER 28, 2021
Cybersecurity incidents aren’t rare for businesses now. In fact, in the first 6 months of 2021, around 1767 data breach incidents rocked the business world and exposed more than 18 billion records. And one of the hardest-hit industry verticals from threatening cyber-attacks is the financial industry.

Security Boulevard
DECEMBER 28, 2021
It’s been another chaotic year in cybersecurity, as protecting web applications and stopping sensitive data breaches remain top-of-mind issues and continue to generate headline news. As 2021 comes to a close, cybersecurity and all the industries it serves is dealing with an unprecedented zero-day vulnerability in the form of CVE-2021-44228 – just 12 months after […].
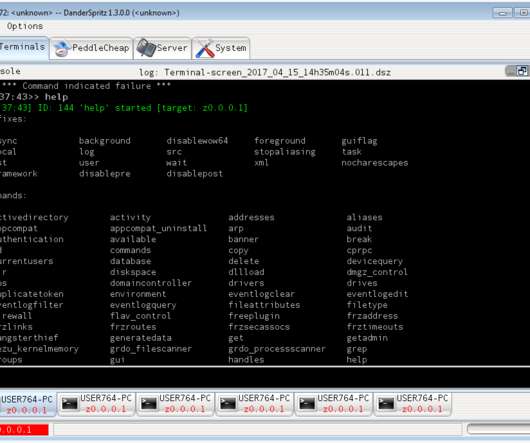
Security Affairs
DECEMBER 28, 2021
Researchers analyzed the DoubleFeature logging tool of DanderSpritz Framework that was used by the Equation Group APT group. Check Point researchers have published a detailed analysis of the DoubleFeature tool used to log post-exploitation activities in attacks conducted by the Equation Group and involving the DanderSpritz malware framework. DanderSpritz made the headlines on April 14, 2017, when it was leaked by the Shadow Broker hacking group along with other tools and exploits belonging to NS

Dark Reading
DECEMBER 28, 2021
To comply with the updated COPPA Rule, online ad platforms need to change how they handle viewers who might be children.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content