Reducing Cybersecurity Risk With Minimal Resources
Lohrman on Security
MARCH 7, 2021
Security Affairs
MARCH 7, 2021
The REvil ransomware operators are using DDoS attacks and voice calls to journalists and victim’s business partners to force victims to pay the ransom. The REvil / Sodinokibi ransomware operators announced that they are using DDoS attacks and voice calls to victim’s business partners and journalists to force the victims into pay the ransom.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
MARCH 7, 2021
Your emails know more about you than you might think, like when you open them or when you forward them to others. But you can reclaim your privacy.

Security Affairs
MARCH 7, 2021
Russia-linked APT groups leveraged the Lithuanian nation’s technology infrastructure to launch cyber-attacks against targets worldwide. The annual national security threat assessment report released by Lithuania’s State Security Department states that Russia-linked APT groups conducted cyber-attacks against top Lithuanian officials and decision-makers last in 2020.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Boulevard
MARCH 7, 2021
Organizations have finally realized that mobile devices are a productivity tool. It became abundantly clear with the sudden necessity of work from home (WFH) that employees work best when they can access a mobile smartphone. One major reason mobile phones are so useful is their integrated camera. The addition of a camera to a smart. The post Keep Your Eye on the Camera appeared first on Security Boulevard.

Bleeping Computer
MARCH 7, 2021
Microsoft has pushed out a new update for their Microsoft Safety Scanner (MSERT) tool to detect web shells deployed in the recent Exchange Server attacks. [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
MARCH 7, 2021
Microsoft has added XLM macro protection for Microsoft 365 customers by expanding the runtime defense provided by Office 365's integration with Antimalware Scan Interface (AMSI) to include Excel 4.0 (XLM) macro scanning. [.].

CyberSecurity Insiders
MARCH 7, 2021
Cloud Misconfigurations are leading to the data exposure of users using android and iOS apps says a research carried out by Zimperium. And what’s surprising in this conformation is that the problems are occurring on platforms launched by world renowned tech companies like Amazon Web Services, Google Cloud, and Microsoft Azure. Another highlight from the research is that a mobile wallet developed by Fortune 500 Company was also involved in exposing information related to users that includes their

Security Affairs
MARCH 7, 2021
Thousands of organizations may have been victims of cyberattacks on Microsoft Exchange servers conducted by China-linked threat actors since January. At least tens of thousands of Microsoft customers may have been hacked by allegedly China-linked threat actors since January, including business and government agencies. The attacks started in January, but the attackers’ activity intensified in recent weeks according to the experts at security firm Volexity.

Trend Micro
MARCH 7, 2021
Rarely do cyber-espionage campaigns appear on the scale of the current Microsoft Exchange Server situation. Four vulnerabilities were exploited by a state-backed threat group linked to China, according to Microsoft.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Thales Cloud Protection & Licensing
MARCH 7, 2021
International Women’s Day 2021: Celebrating Diversity and Inclusiveness. madhav. Mon, 03/08/2021 - 06:53. March 8 is International Women’s Day. With the theme #ChooseToChallenge, this year’s celebration is important to the whole world as the challenge is to call out gender bias and inequality. This day is also important for us at Thales for a very special reason.

Security Affairs
MARCH 7, 2021
The presentation of Williams’s new Formula One car was ruined by hackers that forced the team to abandon the launch through an augmented reality app. The Williams team presented its new Formula One car on Friday, but hackers partially ruined the launch by hacking an “augmented reality” app that was designed to show the new vehicle. The British team, now owned of the American investment firm Dorilton Capital was presenting the new FW43B car, which has “a dramatic new visual identity sportin
Security Boulevard
MARCH 7, 2021
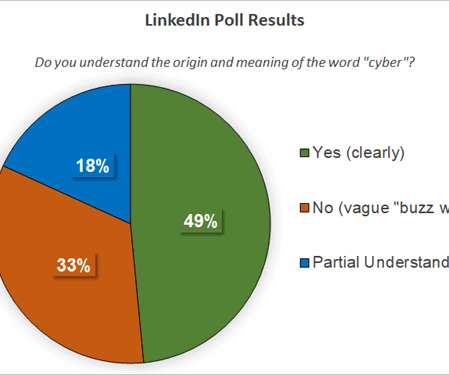
We see the word “cyber” everywhere today. It’s included in all the hashtags, events names and even in hand sanitizer available for purchase at Toys ‘R Us: Cyber Clean (72% ethanol alcohol, with aloe.) With the market booming and the buzzword exploding, many of us still don’t understand what this vague word means. We’re simply […]… Read More. The post The Humanity and Evolution of Cyber appeared first on The State of Security.

CyberSecurity Insiders
MARCH 7, 2021
2020 was a challenging year for cybersecurity teams. They had to secure an unexpected shift to remote work in a matter of days, respond to a surge in BYOD usage, and maintain secure operations without physical access to the resources that they typically use–all without compromising productivity or performance. . During this period, our security research and advisory teams have observed an expansion in the number of different ways that data is exchanged; concurrently, we have observed how

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
MARCH 7, 2021
IBM's 2020 report on the Cost of a Data Breach found that on average it takes 280 days to fix a vulnerability in production once a breach is discovered. If you've got an application in production you may be wondering how you can protect the application once a vulnerability is identified, and before that vulnerability is fixed. The post 280 Days to Fix a Vulnerability in Production appeared first on K2io.

Identity IQ
MARCH 7, 2021
When an identity thief has purchased your personal information from a data breach, they can use it for all manner of malicious purposes. One common use is tax fraud. This means a criminal might have purchased your bank account details and tax documents online and then have authenticated access to your bank account. Then the criminal can file a false tax return on your behalf and claim your refund from the IRS.

Naked Security
MARCH 7, 2021
To this "researcher", even a job not worth doing was worth overdoing. Here's what you can learn from the incident.

SecureBlitz
MARCH 7, 2021
I know what you are thinking – how do I prevent my website from being hacked? Well, we will reveal the best 6 website security platforms. Why Is Website Security Software Essential? Website security software remains the best way of protecting websites from hackers looking out to cause data breaches by hacking and stealing sensitive. The post 6 Best Website Security Platforms [Hacker-Proof LIST] appeared first on SecureBlitz Cybersecurity.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Bleeping Computer
MARCH 7, 2021
Google has added a new feature to Google Chrome Canary that makes it easier for users to test new hidden features under development. [.].

Security Boulevard
MARCH 7, 2021
via the respected information security capabilities of Robert M. Lee & the superlative illustration talents of Jeff Haas at Little Bobby Comics. Permalink. The post Robert M. Lee’s & Jeff Haas’ Little Bobby Comics – ‘WEEK 319’ appeared first on Security Boulevard.

Bleeping Computer
MARCH 7, 2021
Google has added a new feature to Google Chrome Canary that makes it easier for users to test new hidden features under development. [.].

Security Boulevard
MARCH 7, 2021
Change is the one constant in the business world. For most organizations, change often results from market shifts or disruptive technology. Make no mistake, however, the pandemic of 2020 has been a change catalyst. COVID-19 has accelerated digital transformation (DX) across the globe – and at the same time amplified the need to support a [.]. The post Pandemic Unmasks Vulnerability to Automated Bot Attacks appeared first on TechSpective.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Affairs
MARCH 7, 2021
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the international press subscribe here. EU leaders aim at boosting defense and security, including cybersecurity New Zealand-based cryptocurrency exchange Cryptopia hacked again ByteDance agreed to pay $92M in US privacy Settlement for TikTok data collection Gootkit delivery platform Gootloader used to deliv

Security Boulevard
MARCH 7, 2021
Our thanks to BSides Calgary and Conference Speakers for publishing their outstanding presentations; which originally appeared at the group's BSides Calgary 2020 Conference , and on the Organization's YouTube Channel. Enjoy! Permalink. The post BSides Calgary 2020 -Scott Taylor’s ‘Exploring Common Hacking Techniques’ appeared first on Security Boulevard.
SecureBlitz
MARCH 7, 2021
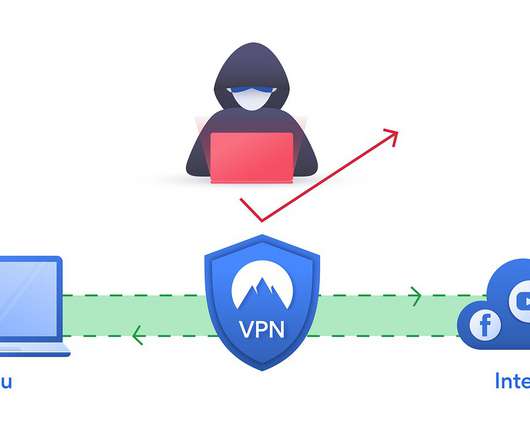
This leaked info contains sensitive device information and login details according to an investigation by CyberNews. According to reports, databases of three main Android VPN applications were leaked recently by a hacker that’s selling 21 million records of users online, which includes sensitive device data and login details, as reported by CyberNews.

Security Boulevard
MARCH 7, 2021
Our thanks to BSides Calgary and Conference Speakers for publishing their outstanding presentations; which originally appeared at the group's BSides Calgary 2020 Conference , and on the Organization's YouTube Channel. Enjoy! Permalink. The post BSides Calgary 2020 – Rick Kaun’s ‘Think Global, Act Local In OT Security’ appeared first on Security Boulevard.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
SecureBlitz
MARCH 7, 2021
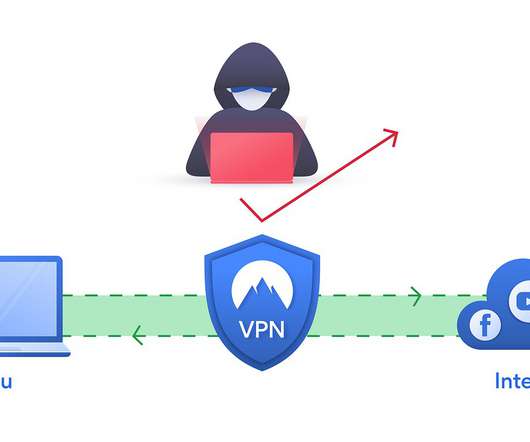
This leaked info contains sensitive device information and login details according to an investigation by CyberNews. According to reports, databases of three main Android VPN applications were leaked recently by a hacker that’s selling 21 million records of users online, which includes sensitive device data and login details, as reported by CyberNews.

Security Through Education
MARCH 7, 2021
In this episode, Chris Hadnagy and Maxie Re ynolds are joined by ex-FBI Spy Catcher and now world renowned Trust and Rapport expert, Robin Dreeke. Listen in as they discuss the importance of mentoring, TRUST and relationship building. – March 8, 2021. Download. Ep. 141 – Do You Want to be Mentored with Robin Dreeke. Get Involved. Got a great idea for an upcoming podcast?

Security Boulevard
MARCH 7, 2021
Deepfake video and audio has really advanced in recent years. Will this technology start to erode trust in the media we consume? Microsoft Exchange zero-days in the wild, and why is it that IT security investment on cybersecurity is at an all time high, yet we continue to see more data breaches? ** Links mentioned […]. The post The Deepfake Dilemma, Microsoft Exchange Zero-Days, IT Security Investments appeared first on The Shared Security Show.
WIRED Threat Level
MARCH 7, 2021
Unlike Google, Brave Search won’t track or profile people who use it.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content