Report: Big U.S. Banks Are Stiffing Account Takeover Victims
Krebs on Security
OCTOBER 7, 2022
When U.S. consumers have their online bank accounts hijacked and plundered by hackers, U.S. financial institutions are legally obligated to reverse any unauthorized transactions as long as the victim reports the fraud in a timely manner. But new data released this week suggests that for some of the nation’s largest banks, reimbursing account takeover victims has become more the exception than the rule.










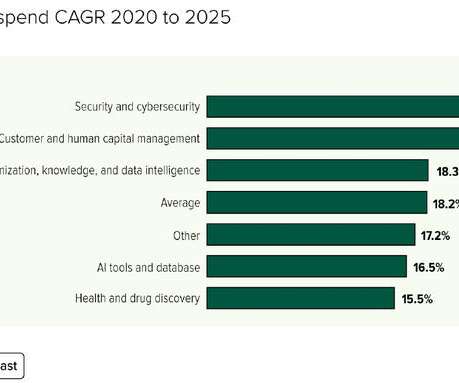






























Let's personalize your content