Contents:
It’s clear that ransomware is one of the biggest threats of today’s cyberscape and the only way to combat it is through information and better choices when it comes to how we use our endpoints and the Internet. For this article, we’ll have a closer look at the Nefilim ransomware strain.
Nefilim Ransomware: History
By definition, ransomware is
a type of malware (malicious software) which encrypts all the data on a PC or mobile device, blocking the data owner’s access to it. After the infection happens, the victim receives a message that tells him/her that a certain amount of money must be paid (usually in Bitcoins) in order to get the decryption key. Usually, there is also a time limit for the ransom to be paid. There is no guarantee that, if the victim pays the ransom, he/she will get the decryption key.
Nefilim ransomware is another ransomware strain that threatens to publish the stolen data if the ransom is not paid, just like Maze, its successor Egregor, and Avaddon. It surfaced and began to spread at the end of February 2020.
The name of this ransomware might have biblical origins. According to Britannica,
Nephilim, in the Hebrew Bible, is a group of mysterious beings or people of unusually large size and strength who lived both before and after the Flood. […] The Hebrew word Nephilim is sometimes directly translated as “giants” or taken to mean “the fallen ones” (from the Hebrew naphal, “to fall”) […]. Some have understood the sons of God to be fallen angels, and the Nephilim are the offspring they produced with human women. This view was described in the First Book of Enoch, a noncanonical Jewish text, and remains a popular explanation.
Nefilim Ransomware: Modus Operandi
Nefilim ransomware places a strong emphasis on Remote Desktop Protocols, brute-forcing RDP setups, and using various known vulnerabilities to gain access. After this, “the attacker drops and executes its components such as anti-antivirus, exfiltration tools, and finally Nefilim itself.”
Nefilim operators use “bat files to stop services/kill processes […], and the stolen credentials are used to reach high-value machines like servers. The hackers work to move around the network before deploying their ransomware to find out where juicier data may be stored. They exfiltrate sensitive data before encryption.”
The data from servers / shared directories is copied to the local directory and compressed using a 7zip binary. After this, MegaSync is installed in order to exfiltrate the data.
Hereafter,
The Nefilim malware uses AES-128 encryption to lock files and their blackmail payments are made via email. After encryption, it drops the ransomware note named ‘NEFILIM-DECRYPT.txt’. All files are encrypted with the extension of (.NEFILIM). It appends AES encrypted key at end of the encrypted file. This AES encryption key will then be encrypted by an RSA-2048 public key that is embedded in the ransomware executable. In addition to the encrypted AES key, the ransomware will also add the “NEFILIM” string as a file marker to all encrypted files.
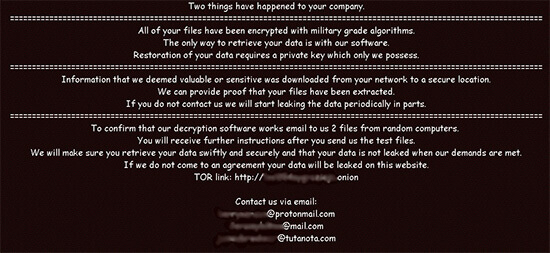
Souse: SISA
Nefilim Ransomware: About Its Targets
The gigantesque traits mentioned in relation to the biblical Nephilims can be found in the status of the companies that become the victims of the Nefilim ransomware operators: they ruthlessly focus on organizations that post more than $1 billion in revenue. However, smaller companies have been hit too.
AS ZD Net writes, “the majority of victims are in the US, followed by Europe, Asia, and Oceania”:
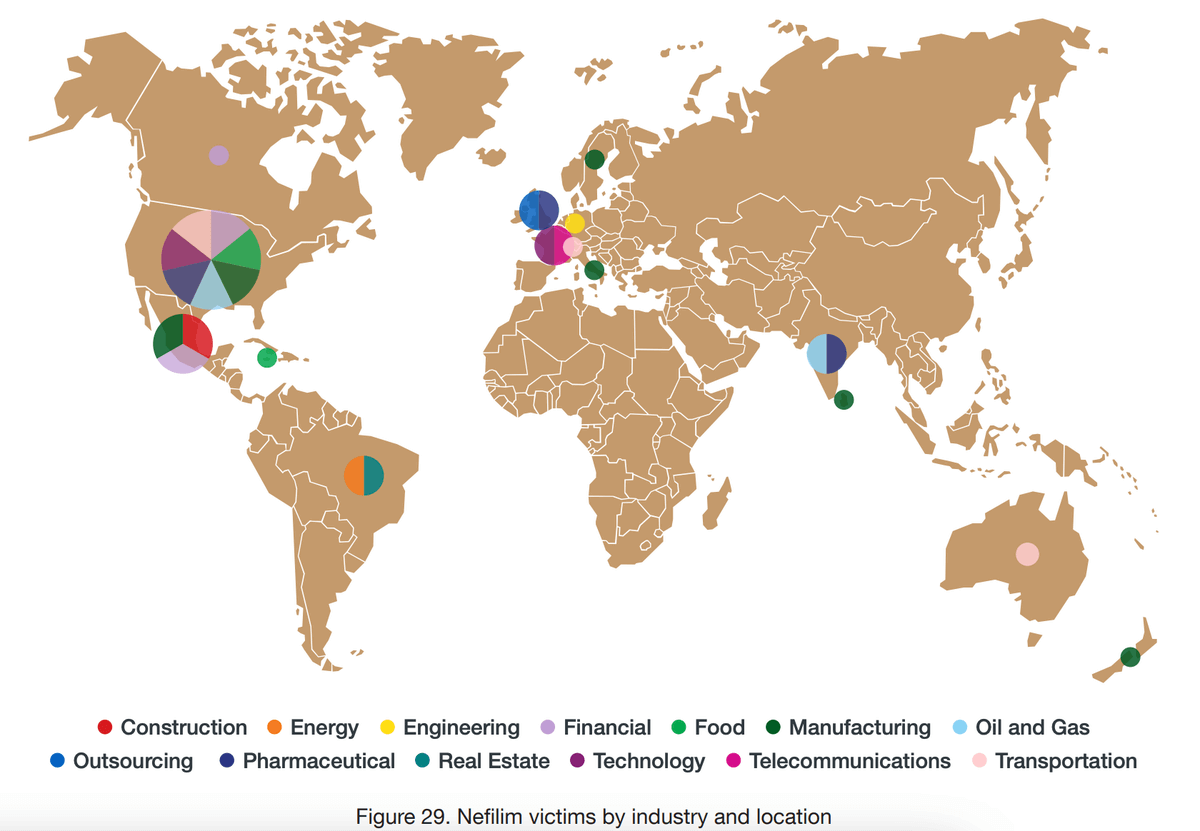
One of the most impressive Nefilim ransomware attacks was directed towards a customer of Sophos Rapid Response, a 24/7 service that helps organizations swiftly identify and neutralize active cyber threats.
What’s impressive about it? The compromised account that the Nefilim ransomware operators used belonged to a person that had passed away around three months before the attack started, which demostrates once again how privileged accounts can compromise your security.
Nefilim Ransomware: Next Steps in Case of Attack
Although we’ll discuss prevention strategies below, let us pretend for now that the worst-case scenario came true and you were targeted by the Nefilim ransomware operators. What should you do at this point?
- Check if your RDP connection is open to the Internet – it shouldn’t.
- If you’re not using an RDP, close the TCP Port 3389 on your endpoints.
- Block the indicators of compromise (IOCs).
Should you pay the ransom?
The FBI would advise you not to:
In some cases, victims who paid a ransom were never provided with decryption keys. In addition, due to flaws in the encryption algorithms of certain malware variants, victims may not be able to recover some or all of their data even with a valid decryption key. Paying ransoms emboldens criminals to target other organizations and provides an alluring and lucrative enterprise to other criminals. However, the FBI understands that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers. Regardless of whether you or your organization have decided to pay the ransom, the FBI urges you to report ransomware incidents to law enforcement. Doing so provides investigators with the critical information they need to track ransomware attackers, hold them accountable […], and prevent future attacks.
- Consequently, the next step would be to contact the authorities.
Nefilim Ransomware: Prevention Strategy
How should you approach the topic of prevention strategy and avoid becoming the next victim of the Nefilim ransomware? Well, as with any other ransomware strain, you need a layered defense that should include:
Patch Management
Patch management will help you keep your system and software up-to-date, closing the vulnerabilities that often lead to ransomware attacks.
Heimdal® Patch & Asset Management Software
Email Security
Advance email security solutions can secure your business email agents against malware and ransomware delivered via email and will keep messages that contain spam, phishing, and malicious URL’s out of your inbox.
Ransomware Protection
A ransomware encryption protection module is actually the latest addition to our product suite – it offers your network powerful HIPS\HIDS capabilities, detecting and resolving any APTs that may linger on your network. Moreover, it is compatible with any antivirus solution on the market.
Heimdal™ Ransomware Encryption Protection
Security Awareness Training
For a ransomware infection to happen, sometimes all it takes is an employee clicking on a compromised link or attachment in an email. Consequently, security awareness training programs for all employees are essential.
Nefilim Ransomware: Final Thoughts
Nefilim ransomware is a new, serious threat to big companies, but it also targets smaller ones. For this reason, prevention and a good cybersecurity posture should be on the list of priorities of any business owner.
However you choose to proceed, please remember that Heimdal™ Security always has your back and that our team is here to help you protect your home and your company and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it.
Drop a line below if you have any comments, questions, or suggestions related to the topic of the Nefilim ransomware – we are all ears and can’t wait to hear your opinion!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











