Norton’s Antivirus Product Now Includes an Ethereum Miner
Schneier on Security
JANUARY 7, 2022
Norton 360 can now mine Ethereum. It’s opt-in, and the company keeps 15%. It’s hard to uninstall this option.

Schneier on Security
JANUARY 7, 2022
Norton 360 can now mine Ethereum. It’s opt-in, and the company keeps 15%. It’s hard to uninstall this option.

Tech Republic Security
JANUARY 7, 2022
The new opt-in feature turns your idle PC into a cryptominer, with Norton skimming 15% off the top, plus market fees.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
JANUARY 7, 2022
SonicWall has confirmed today that some of its Email Security and firewall products have been hit by the Y2K22 bug, causing message log updates and junk box failures starting with January 1, 2022. [.].

Security Boulevard
JANUARY 7, 2022
On Tuesday, the United States Federal Trade Commission (FTC) issued a stern warning to companies that have not yet patched the Log4j vulnerability: We will find you. The post Cybersecurity News Round-Up: Week of January 3, 2022 appeared first on Security Boulevard.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Bleeping Computer
JANUARY 7, 2022
The US National Counterintelligence and Security Center (NCSC) and the Department of State have jointly published guidance on defending against attacks using commercial surveillance tools. [.].

Security Boulevard
JANUARY 7, 2022
It seems like users are now paying the price for Google not fully closing or mitigating a vulnerability in the comment feature of Google Docs—since December a “massive wave” of hackers have exploited the flaw through impersonation and phishing to send malicious content to those using email—primarily Outlook—and Google Docs, according to researchers at Avanan.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The State of Security
JANUARY 7, 2022
Security researchers say they have seen a "massive wave" of hackers exploiting the comment feature in Google Docs to spread malicious content into the inboxes of unsuspecting targeted users. Read more in my article on the Tripwire State of Security blog.

Security Boulevard
JANUARY 7, 2022
Yes, the French are revolting (again): France plans to hit Google and Facebook/Meta with $240 million in fines (€210M). The post Facebook/Google use Dark Patterns in Cookie Consent—says France, Waving $240M Fines appeared first on Security Boulevard.

Security Affairs
JANUARY 7, 2022
The appointment scheduling service FlexBooker discloses a data breach that impacted over 3.7 million accounts. Threat actors compromised the FlexBooker accounts of more than 3.7 million users, the attack took place before the holidays. Stolen data are now available for sale on multiple cybercrime forums. FlexBooker is an online appointment scheduling platform that allows users to schedule appointments and sync employee calendars.
Security Boulevard
JANUARY 7, 2022
Originally published by Robert Ronan, Oracle Principal Product Manager. What is zero trust access? As more organizations migrate infrastructure to the cloud and rethink software development and deployment, they are also modernizing their approach to security. One such approach is Zero Trust – instead of relying on traditional network perimeter-based security tools such as VPNs […].

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

CyberSecurity Insiders
JANUARY 7, 2022
In a case related to cookie tracking of online users, France’s Data Privacy Watchdog slapped a hefty penalty of €210m for stopping companies from snooping on online users. The Commission Nationale de l’Informatique et des Libertes (CNIL) said that penalty was split between two companies, with Google being slapped with €150m for making it difficult for online users to refuse cookie pop-ups.

Security Boulevard
JANUARY 7, 2022
When assessing risk in your organization, the first step is to define the scope of your information assets, especially those which could impact the confidentiality, integrity and accessibility of information within your company. That includes any risks that affect assets that process, store and transmit personal data. You can reduce and nullify these risks with.

CSO Magazine
JANUARY 7, 2022
The UK’s National Cyber Security Centre (NCSC) is updating its requirements for the Cyber Essentials scheme, a government-backed certification that helps UK organisations defend against common cyberthreats. The update is in response to the evolving cybersecurity challenges that organisations now face and represents the most significant overhaul of the scheme’s technical controls since it was launched in 2014.

Bleeping Computer
JANUARY 7, 2022
The widely distributed FluBot malware continues to evolve, with new campaigns distributing the malware as Flash Player and the developers adding new features. [.].

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Security Affairs
JANUARY 7, 2022
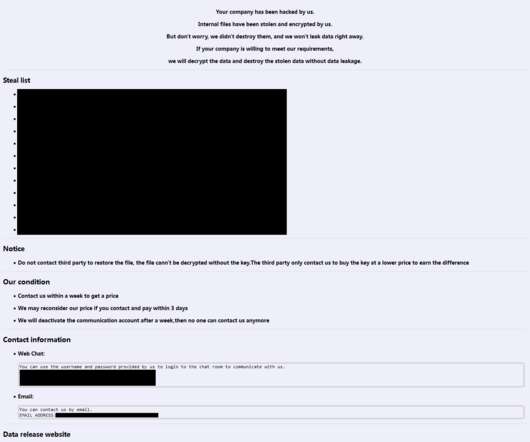
Researchers warn of a new ransomware family, called ‘Night Sky,’ that uses a double-extortion model in attacks again businesses. Researchers from MalwareHunterteam first spotted a new ransomware family dubbed Night Sky that implements a double extortion model in attacks aimed at businesses. Once encrypted a file, the ransomware appends the ‘ nightsky ‘ extension to encrypted file names.

Security Boulevard
JANUARY 7, 2022
New York Attorney General Letitia James has put 17 companies on notice that 1.1 million online accounts have been compromised by cyberattacks involving credential stuffing. In a “Business Guide for Credential Stuffing Attacks” that described her office’s investigation, the AG provided details on the attacks and how, through automated attempts using usernames and passwords nicked.

We Live Security
JANUARY 7, 2022
And no more worrying about your satellite being smashed by a “drunk driver” as new tech promises to predict hazards in orbit. The post CES 2022: Space security – no more flying blind appeared first on WeLiveSecurity.

The Hacker News
JANUARY 7, 2022
Researchers have disclosed a security flaw affecting H2 database consoles that could result in remote code execution in a manner that echoes the Log4j "Log4Shell" vulnerability that came to light last month.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
JANUARY 7, 2022
“We informed a very small number of customers that the SIM card assigned to a mobile number on their account may have been illegally reassigned or limited account information was viewed,” a T-Mobile spokesperson told BleepingComputer last week in response to questions about a new T-Mobile data breach. “This issue was quickly corrected by our team, using our in-place safeguards, and we proactively took additional protective measures on their behalf,” the spokesperson added.

Threatpost
JANUARY 7, 2022
There are active ransomware and brute-force attacks being launched against internet-exposed, network-attached storage devices, the device maker warned.

Security Boulevard
JANUARY 7, 2022
Running a successful EDR platform and MDR service is never-ending pursuit to stay one step ahead of hackers. As threat actors find creative ways to attempt to circumvent our customers defenses, we are constantly innovating to ensure we can detect and respond to security incidents quickly. Our founders Chris Gerritz and Russ Morris joined me…. The post Under the Hood of an MDR Company: an Exercise in Innovation [Video] appeared first on Infocyte.

CyberSecurity Insiders
JANUARY 7, 2022
A ransomware attack on FinalSite, a SaaS service provider to multiple universities and K-12 school districts in United States disrupted access to websites and digital services related to many educational institutions. Finalsite has apologized for the digital shutdown that could have affected more than 5K out of 8K schools operating in America (mainly those operating in Missouri, Kansas, Illinois, and Minnesota) and multiple Universities across 110 various countries.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Bleeping Computer
JANUARY 7, 2022
With the holidays these past two weeks, there have been only a few known ransomware attacks and little research released. Here is what we know. [.].

Dark Reading
JANUARY 7, 2022
The most successful strategies for protecting IT and OT from growing threats will include use of both the ISO 27000 series and ISA/IEC 62443 family of standards.

Malwarebytes
JANUARY 7, 2022
Finalsite, a popular platform for creating school websites, appears to have recovered significant functionality after being attacked by a still-unknown ransomware on Tuesday, January 4, 2022. At least 8,000 schools are said to have been affected by the resulting outage. An important message from Finalsite: pic.twitter.com/BXW5dzfJS3 — Finalsite (@Finalsite) January 6, 2022.

Security Boulevard
JANUARY 7, 2022
As December 2021 came to a close, indicted and arrested Russian national Vladislav Klyushin was quietly extradited from Switzerland to the United States. A spokesperson for the Russian Embassy in Switzerland, Vladimir Khokhlov, was quoted by TASS and Radio Free Europe/Radio Liberty, saying, “We are forced to state that we are dealing with another episode.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Bleeping Computer
JANUARY 7, 2022
The Federal Bureau of Investigation (FBI) warned US companies in a recently updated flash alert that the financially motivated FIN7 cybercriminal group targeted the US defense industry with packages containing malicious USB devices to deploy ransomware. [.].
Security Boulevard
JANUARY 7, 2022
To better understand what differentiates successful security operations, we are conducting the 2022 Security Operations Benchmark Study. The post What differentiates successful security operations? appeared first on Topo.ai. The post What differentiates successful security operations? appeared first on Security Boulevard.

Bleeping Computer
JANUARY 7, 2022
UK's National Health Service (NHS) has published a cyber alert warning of an unknown threat group targeting VMware Horizon deployments with Log4Shell exploits. [.].

Security Boulevard
JANUARY 7, 2022
As is often the case with Active Directory, some of the worst security gaps are caused by misconfigurations that leave open doors for cyberattackers. One common setting that cybercriminals love to exploit is unconstrained delegation. What is unconstrained delegation, and why is unconstrained delegation a security risk? Delegation is the action of allowing a computer.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content