Global Cybersecurity Ramifications from the War in Ukraine
Lohrman on Security
MARCH 20, 2022
What have we learned so far regarding cybersecurity from the Russia-Ukraine war and related cyber incidents around the world? Let’s explore.

Lohrman on Security
MARCH 20, 2022
What have we learned so far regarding cybersecurity from the Russia-Ukraine war and related cyber incidents around the world? Let’s explore.

Security Boulevard
MARCH 20, 2022
Learn what DDoS is and what it can do to your API endpoints, how to mitigate DDOS attacks, and build a security response. The post How to Mitigate DDoS Attacks on Your APIs appeared first on Traceable App & API Security. The post How to Mitigate DDoS Attacks on Your APIs appeared first on Security Boulevard.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Acunetix
MARCH 20, 2022
Weak passwords and password reuse are still some of the most serious concerns for cybersecurity. There are several ways to increase password security but they are often not adopted by users and administrators. Here’s how you can make sure that sensitive data in your web. Read more. The post Common password vulnerabilities and how to avoid them appeared first on Acunetix.

Security Boulevard
MARCH 20, 2022
Thanks are in order to the Munich Security Conference) for the yearly publishing of their terrific videos covering the Munich Security Conference on the organization’s YouTube channel. This embedded compilation provides over 4 and 1/2 hours of cybersecurity & information security content from the Munich Cybersecurity Conference held earlier this year, and not previously published here.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Affairs
MARCH 20, 2022
Anonymous hacked Omega Company, the in-house R&D unit of Transneft, the Russian oil pipeline giant, and leaked stolen data. Anonymous collective claims it has hacked Omega Company, which is the in-house R&D unit of Transneft, the Russia-based state-controlled oil pipeline company. Transneft is the largest oil pipeline company in the world, the hacktivists have stolen 79GB of emails and published them on the leak site of the non-profit whistleblower organization Distributed Denial of Secr
Security Boulevard
MARCH 20, 2022
Russia, Belarus, and China have taken some definite steps towards breaking off their internet into a separate entity that is controlled by the state. Russia has had a history of conducting tests to disconnect itself from the internet. China has already its version of the WWW complete with an ecosystem of developers and government controls. […]. The post Splinternet will lead to the evolution of new and sophisticated malware appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Boulevard
MARCH 20, 2022
STEM summer camps can make summer learning fun and exciting by teaching kids about science, technology, engineering, and math. The camps can give children an opportunity to continue learning more about a concept they were introduced to during the school year or event explore different STEM concepts they may not learn about in their classrooms. The post Benefits of STEM Summer Camps first appeared on SecurityOrb.com.

Heimadal Security
MARCH 20, 2022
Whether we use it mostly at home or at work, the Internet is not always a safe place – clearly. As cybersecurity professionals, we know – and try to draw everyone’s attention too – that there are dozens of threats we need to be aware of in order to protect our online security. In this […]. The post Riskware. Cybersecurity Threats You Must Be Aware Of appeared first on Heimdal Security Blog.

Bleeping Computer
MARCH 20, 2022
Western Digital's EdgeRover desktop app for both Windows and Mac are vulnerable to local privilege escalation and sandboxing escape bugs that could allow the disclosure of sensitive information or denial of service (DoS) attacks. [.].

Security Affairs
MARCH 20, 2022
This post provides a timeline of the events related to the Russia invasion of Ukraine from the cyber security perspective. Below is the timeline of the events related to the previous weeks: March 18 – China-linked threat actors are targeting the government of Ukraine. Google’s TAG team revealed that China-linked APT groups are targeting Ukraine ’s government for intelligence purposes.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

WIRED Threat Level
MARCH 20, 2022
A brief history and the ramifications of cluster bombs, history’s most indiscriminate weapon.

Security Boulevard
MARCH 20, 2022
Endpoint devices played a big part in malware and ransomware attacks in 2021. According to a study covered by Help Net Security, security researchers detected more malware and ransomware endpoint infections in the first nine months of the year than they did for all of 2020. Attack scripts leveraging PowerSploit, Cobalt Strike, and other tools […]… Read More.

WIRED Threat Level
MARCH 20, 2022
Lock down your account to tweet in peace or take the guardrails off to court controversy.

Security Boulevard
MARCH 20, 2022
This week we discuss the top 3 location tracking apps in the Apple App Store and Google Play and which ones sell your data. Plus, details about recent fake Chick-fil-A and Olive Garden vouchers on Facebook. ** Links mentioned on the show ** #1 Phone Tracker by Number [link] [link] – Android [link] – iOS […]. The post Top 3 Location Tracking Apps: Do They Sell Your Data?

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Daniel Miessler
MARCH 20, 2022
I’m starting a new series with this 2022 edition where I think about what Information Security could or should look like in the distant future—say in 2050. The ideas will cover multiple aspects of InfoSec, from organizational structure to technology. I’m doing this for fun—basically to see how dumb I look later—but I also hope it’ll drive interesting discussions on where things should go.

Security Boulevard
MARCH 20, 2022
Our thanks to Purdue University’s The Center for Education and Research in Information Assurance and Security (CERIAS) for publishing their illuminating security symposiums, seminars, talks, and presentations on the Schools’ YouTube channel. Permalink. The post Purdue University’s CERIAS 2021 Security Symposium – Ida Ngambeki, PhD’s ‘Industrial Control Systems Security: An Educational Challenge’ appeared first on Security Boulevard.
Security Affairs
MARCH 20, 2022
FBI, CISA, and the European Union Aviation Safety Agency (EASA) warn of possible threats to international satellite communication (SATCOM) networks. Satellite communication (SATCOM) networks are critical infrastructure for modern society, US and EU agencies warn of possible threats to them. Victor Zhora, Chief Digital Transformation Officer at the State Service of Special Communication and Information Protection (SSSCIP) of Ukraine, speaking about the VIASAT attack , said “it was a really
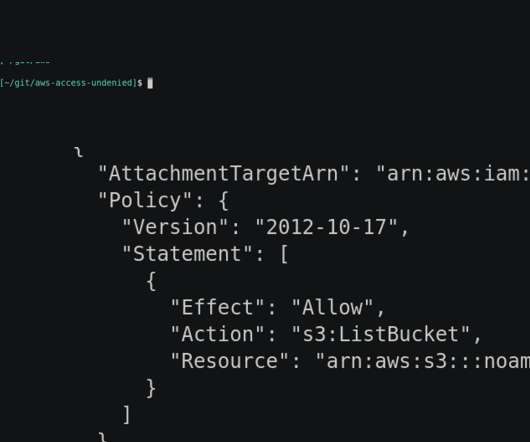
Security Boulevard
MARCH 20, 2022
Ermetic is launching a new open-source tool: Access Undenied on AWS. The tool parses AWS AccessDenied CloudTrail events, explains the reasons for them and offers actionable fixes. The post Access Undenied on AWS appeared first on Ermetic. The post Access Undenied on AWS appeared first on Security Boulevard.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Affairs
MARCH 20, 2022
A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the newsletter with the international press subscribe here. EU and US agencies warn that Russia could attack satellite communications networks Avoslocker ransomware gang targets US critical infrastructure Crooks claims to have stolen 4TB of data from TransUnion South Africa Exotic Lily initial access broker
Security Boulevard
MARCH 20, 2022
via the comic artistry and dry wit of Randall Munroe , resident at XKCD ! Permalink. The post XKCD ‘Advanced Techniques’ appeared first on Security Boulevard.

Security Boulevard
MARCH 20, 2022
One of the main challenges of OT security is the problem of compatibility. OT components often differ significantly from each other in terms of age and sophistication as well as software and communication protocols. This complicates asset discovery and makes it difficult to establish a consistent cybersecurity governance approach. Combating asset blindness in OT security […]… Read More.
Let's personalize your content