How to check if your info was exposed in the Facebook data leak
Bleeping Computer
APRIL 4, 2021
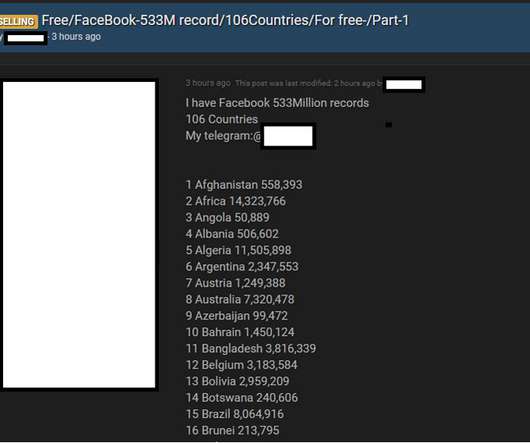
Data breach notification service Have I Been Pwned can now be used to check if your personal information was exposed in yesterday's Facebook data leak that contains the phone numbers and information for over 500 million users. [.].

























Let's personalize your content