Scam Alert: Impersonating Law Enforcement, Doxxing and Swatting
Lohrman on Security
MAY 1, 2022
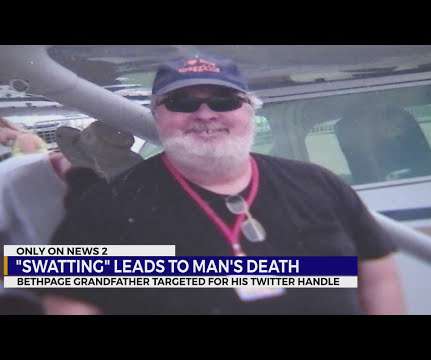
Criminals are using stolen information to imitate the police and scam both companies and individuals. Here’s what you need to know.
Lohrman on Security
MAY 1, 2022
Criminals are using stolen information to imitate the police and scam both companies and individuals. Here’s what you need to know.
Security Boulevard
MAY 1, 2022
In the past, I’ve written about digital privacy and how much data we leak through our day to day interactions. I think this is an important topic to consider and really focus on and it is an element of cybersecurity at both the enterprise and personal level that isn’t discussed enough. One of the reasons […]… Read More. The post OSINT: The privacy risks of sharing too much information appeared first on The State of Security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CyberSecurity Insiders
MAY 1, 2022
A Texas school district has hit Google headlines as one of its employees was caught mining cryptocurrency without permission of the school management or the government officials. Galveston Independent School District (Galveston ISD) is the educational institution in discussion and the name of the employee found guilty is withheld. According a source reporting from the IT department of Galveston Independent School District (GISD), an employee has installed cryptocurrency mining hardware and softw

Trend Micro
MAY 1, 2022
We found an AvosLocker ransomware variant using a legitimate anti-virus component to disable detection and blocking solutions.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

CyberSecurity Insiders
MAY 1, 2022
All these days we have been discussing Distributed Denial of Service attacks aka Ddos attacks and the massive amounts of fake traffic they create to network disruptions in corporate and government networks. But Yo-Yo DDoS Attack is different and seems to be an innovative way to attack public cloud infrastructures. Technically, they target cloud architecture’s auto-scaling capabilities to hurt those allocated with a portion of blobs on a financial note.

Bleeping Computer
MAY 1, 2022
The notorious REvil ransomware operation has returned amidst rising tensions between Russia and the USA, with new infrastructure and a modified encryptor allowing for more targeted attacks. [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
MAY 1, 2022
The Open Source Security Foundation (OpenSSF), a Linux Foundation-backed initiative has released its first prototype version of the 'Package Analysis' tool that aims to catch and counter malicious attacks on open source registries. the open source tool released on GitHub was able to identify over 200 malicious npm and PyPI packages. [.].
Security Boulevard
MAY 1, 2022
Criminals are using stolen information to imitate the police and scam both companies and individuals. Here’s what you need to know. The post Scam Alert: Impersonating Law Enforcement, Doxxing and Swatting appeared first on Security Boulevard.

Bleeping Computer
MAY 1, 2022
Google has expanded its policies to allow doxxing victims to remove more of their personally identifiable information (PII) from search engine results starting earlier this week. [.].

Security Boulevard
MAY 1, 2022
As part of our mission to help organisations protect their data and all paths to it, Imperva is supporting Privacy Awareness Week in Australia and Singapore, with the aim of educating individuals and organisations about the importance of data privacy and protection. In today’s digital economy, data is the new oil. The problem is: when […]. The post Data Protection as the Foundation of Trust: Celebrating Privacy Awareness Week in APAC appeared first on Blog.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

The Hacker News
MAY 1, 2022
The Open Source Security Foundation (OpenSSF) has announced the initial prototype release of a new tool that's capable of carrying out dynamic analysis of all packages uploaded to popular open source repositories.

Security Affairs
MAY 1, 2022
Threat actors exploited a bug in the Fuse protocol used by DeFi platforms Rari Capital and Fei Protocol and stole more than $80 million. Threat actors stole more than $80 million from the decentralized finance (DeFi) platforms Rari Capital and Fei Protocol on Saturday. Researchers from smart contract analysis firm Block Sec reported that attackers exploited a reentrancy bug in Rari’s Fuse lending protocol.

The Hacker News
MAY 1, 2022
Google has officially released the first developer preview for the Privacy Sandbox on Android 13, offering an "early look" at the SDK Runtime and Topics API to boost users' privacy online. "The Privacy Sandbox on Android Developer Preview program will run over the course of 2022, with a beta release planned by the end of the year," the search giant said in an overview.

WIRED Threat Level
MAY 1, 2022
Maybe you don't want your phone number, email, home address, and other details out there for all the web to see. Here's how to make them vanish.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Affairs
MAY 1, 2022
Synology warns customers that some of its NAS devices are affected by multiple critical Netatalk vulnerabilities. Synology has warned customers that multiple critical Netatalk vulnerabilities affect some of its network-attached storage (NAS) devices. Netatalk is a free, open-source implementation of the Apple Filing Protocol that allows Unix-like operating systems to serve as a file server for macOS computers.

Bleeping Computer
MAY 1, 2022
Security analysts have uncovered a recent phishing campaign from Russian hackers known as APT29 (Cozy Bear or Nobelium) targeting diplomats and government entities. [.].

Security Affairs
MAY 1, 2022
This post provides a timeline of the events related to the Russian invasion of Ukraine from the cyber security perspective. Below is the timeline of the events related to the ongoing invasion that occurred in the previous weeks: April 30 – Pro-Russian group Killnet launched DDoS attacks on Romanian govt sites. A series of DDoS attacks launched by Russian hacktivists are targeting several Romanian government websites.

Bleeping Computer
MAY 1, 2022
A YouTube influencer with hundreds of thousands of subscribers is encouraging everyone to conduct cyber warfare against Russia. How risky is it and can you get in trouble? [.].

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

The State of Security
MAY 1, 2022
Tripwire’s April 2022 Patch Priority Index (PPI) brings together important vulnerabilities for Microsoft, Google Chrome, Oracle, and Adobe. First on the patch priority list this month is an elevation of privilege vulnerability in the Microsoft Windows User Profile Service. This vulnerability has been added to the Metasploit Exploit Framework and any vulnerable systems should be […]… Read More.

Security Affairs
MAY 1, 2022
A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the newsletter with the international press subscribe here. Microsoft Azure flaws could allow accessing PostgreSQL DBs of other customers Emotet tests new attack chain in low volume campaigns Pro-Russian group Killnet launched DDoS attacks on Romanian govt sites Anonymous hacked Russian PSCB Commercial Ba

SecureWorld News
MAY 1, 2022
Travel can involve significant security risks. Employees may be exposed to new safety threats, whether they're moving within the country or abroad—including physical threats and cybersecurity dangers. Organizations of all kinds have a responsibility to keep their employees safe while they're traveling. These are the threats workers may face and what enterprises can do to protect them.
WIRED Threat Level
MAY 1, 2022
Your Microsoft computer comes with built-in safety software that shields you from the worst threats. Here's how to navigate your toolkit.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Boulevard
MAY 1, 2022
Tripwire’s April 2022 Patch Priority Index (PPI) brings together important vulnerabilities for Microsoft, Google Chrome, Oracle, and Adobe. First on the patch priority list this month is an elevation of privilege vulnerability in the Microsoft Windows User Profile Service. This vulnerability has been added to the Metasploit Exploit Framework and any vulnerable systems should be […]… Read More.
Security Affairs
MAY 1, 2022
Russia-linked APT29 (Cozy Bear or Nobelium) launched a spear-phishing campaign targeting diplomats and government entities. In mid-January 2022, security researchers from Mandiant have spotted a spear-phishing campaign, launched by the Russia-linked APT29 group, on targeting diplomats and government entities. The Russia-linked APT29 group (aka SVR , Cozy Bear , and The Dukes ) has been active since at least 2014, along with APT28 cyber espionage group was involved in the Democratic National Comm

Security Boulevard
MAY 1, 2022
Elon Musk buys Twitter for $44 billion so what does this mean for the privacy and cybersecurity of the platform? More than 100 different Lenovo laptop computers contain firmware-level vulnerabilities which is a great reminder about making sure you update the BIOS on your computer. Plus, details about researchers who have created a t-shirt that […]. The post Elon Musk Buys Twitter, Forgotten BIOS Updates, T-Shirt Outwits Facial Recognition appeared first on The Shared Security Show.

Security Boulevard
MAY 1, 2022
Our thanks to both the OWASP® Foundation and the OWASP Global AppSec US 2021 Virtual Conference for publishing their well-crafted application security videos on the organization’s’ YouTube channel. Permalink. The post OWASP® Global AppSec US 2021 Virtual – Rob Dickinson’s OWASP Cautions Against “Insufficient Logging & Monitoring” What Does Sufficient Look Like?

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Boulevard
MAY 1, 2022
Our thanks to both the OWASP® Foundation and the OWASP Global AppSec US 2021 Virtual Conference for publishing their well-crafted application security videos on the organization’s’ YouTube channel. Permalink. The post OWASP® Global AppSec US 2021 Virtual – Michele Chubirka’s ‘Container Security: It’s All About The Supply Chain’ appeared first on Security Boulevard.
Security Boulevard
MAY 1, 2022
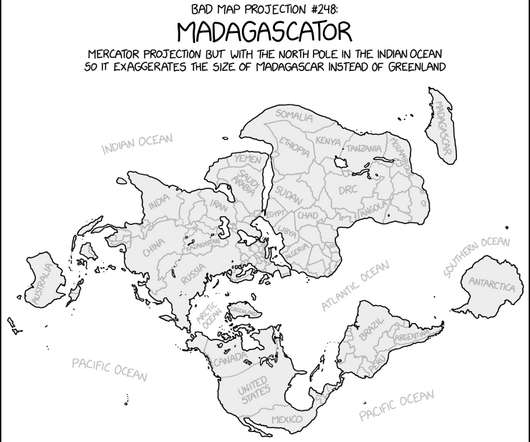
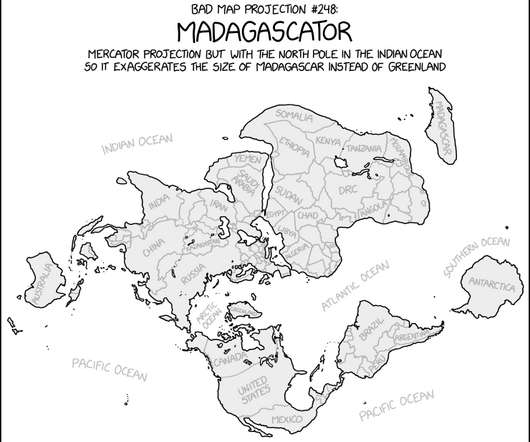
via the comic artistry and dry wit of Randall Munroe , resident at XKCD ! Permalink. The post XKCD ‘Bad Map Projection: Madagascator’ appeared first on Security Boulevard.
Let's personalize your content