Dissection of the recent SUNBURST attack campaign provides crucial threat intelligence for strategic action.

The SolarWinds Orion SUNBURST backdoor is a sophisticated attack that creates a challenging problem for threat hunters (and data scientists) to solve. The attack has had a large impact through its clever design, and we can assume that we haven’t seen the full extent of damage yet. It is worth deconstructing the available data for more indicators of compromise that might add valuable threat intelligence to the security community for future attacks.
The FireEye blog post identified several domains that are associated with the SUNBURST attack campaign: “avsvmcloud[.]com”, “freescanonline[.]com”, “thedoccloud[.]com”, “deftsecurity[.]com”, websitetheme[.]com”, “highdatabase[.]com”, “incomeupdate[.]com”, “databasegalore[.]com”, “panhardware[.]com”, and “zupertech[.]com”.
Open-Source Intelligence (OSINT) tools show that “avsvmcloud[.]com” was originally registered around July 25, 2018, was purchased through a domain reseller around February 26, 2020, and was dormant prior to February 26, 2020.
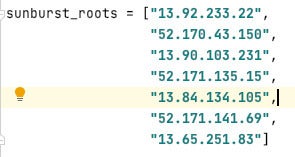
Digging further into the OSINT data, we see that avsvmcloud[.]com was assigned the following IP addresses as DNS type A records.
 ExtraHop
ExtraHopNo further activity is seen until April 15th, when we see an algorithmically-generated hostname that matches the “avsvmcloud” command-and-control node described in the FireEye blog post: “f526qtbk9bbb9chpf1vt24i.appsync-api.eu-west-1.avsvmcloud[.]com”.
After April 15, DNS resolutions show between 0 and 17 unique addresses per day formed from the algorithm-generated hostname plus a variable geolocation subdomain (such as us-east-2, us-east-1, eu-west-1, us-west-1). We can surmise that the gaps in the data stream are due to the short and sparse communications with the command-and-control servers and the ephemeral nature of DNS records for command-and-control servers.
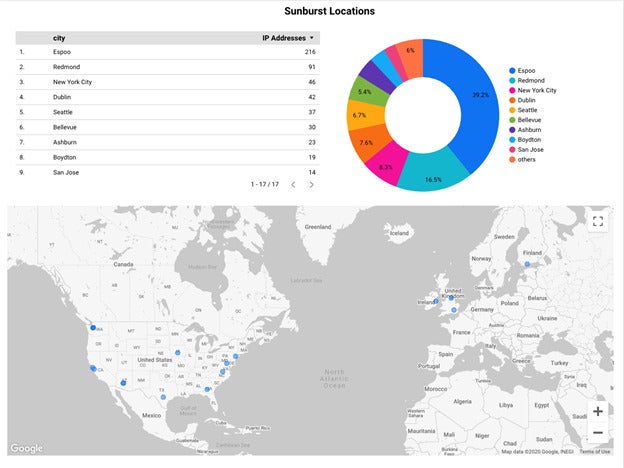
The following map identifies the approximate regions of these servers:
 ExtraHop
ExtraHopWhat Can Security Analysts Do?
Search your network logs for the suspicious IP addresses that were associated with the attack in this downloadable JSON text file. Any client that has connected to one of these IP addresses might be affected by the SUNBURST trojan, and we recommend that you take steps to remediate the attack as provided on the SolarWinds website.
We’ve determined that looking for current activity alone is insufficient. The SUNBURST trojan is dormant for long periods of time and might only occasionally perform DNS resolutions. ExtraHop collects extensive historical metadata and metrics, which can be queried to hunt for specific threats.
Due to the size of the list, we recommend that ExtraHop users run the script in the following directory (sunburst) through the REST API.
For more information, contact your ExtraHop representative or send a request for help through our website.
References
This analysis was developed with ExtraHop proprietary tools and OSINT tools. The primary sources of information are historical databases that contain both active and passive collections of DNS records, DNS registration information, as well as other active probes.








