Practical Ways Older Adults Can Manage Their Security Online
Lohrman on Security
JANUARY 31, 2021

Security Boulevard
JANUARY 31, 2021
The pandemic and resulting migration to remote work emphasized the importance of having a digital transformation process in place. The companies that did so appeared to be the companies that had the smoothest transition. Cloud computing played a pivotal role, allowing employees to have the access they needed to do their work. The downside was. The post Taking a Data-Centric Approach to Cloud Security appeared first on Security Boulevard.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Graham Cluley
JANUARY 31, 2021
The website of Mensa - the club for people who have scored highly in an IQ test but who feel their social lives would be improved by hanging out with other people who chose to join a club after scoring highly in an IQ test - is said to have suffered a cyber attack. Coincidentally (or not) the news comes as a board member of British Mensa resigns, citing poor password security.

Security Boulevard
JANUARY 31, 2021
While the U.S. government was focused on election security last year, unbeknownst to senior American officials a secret cyber espionage campaign by a major nation-state adversary of unprecedented magnitude was already underway – lethal, stealthy and undetected. In early December 2020, the U.S. cybersecurity firm FireEye Inc. announced that it had been the victim of a.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Affairs
JANUARY 31, 2021
Expert disclosed an unpatched vulnerability in Microsoft Azure Functions that could be exploited to escape the Docker container hosting them. Cybersecurity researcher Paul Litvak from Intezer Lab disclosed an unpatched vulnerability in Microsoft Azure Functions that could be exploited by an attacker to escalate privileges and escape the Docker container that hosts them.

Security Boulevard
JANUARY 31, 2021
Have you ever wanted to help your parents or an elderly friend or relative by providing an online resource that is both informative, offers practical tips and definitions about security, and is also easy to understand? I have, and the new book Senior Cyber by Scott and Craig Schober offers that helpful guide you’ve been. The post Practical Ways Older Adults Can Manage Their Security Online appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Affairs
JANUARY 31, 2021
Experts from Great Firewall Report analyzed recent upgrades to China’s Great Firewall and revealed that it can be circumvented. Members of the Great Firewall Report group have analyzed the recent improvement implemented for China’s Great Firewall censorship system and revealed that it is possible to bypass it.

The Hacker News
JANUARY 31, 2021
A "severe" vulnerability in GNU Privacy Guard (GnuPG)'s Libgcrypt encryption software could have allowed an attacker to write arbitrary data to the target machine, potentially leading to remote code execution. The flaw, which affects version 1.9.

Identity IQ
JANUARY 31, 2021
Life is hectic and it’s easy to miss details sometimes, even when that detail happens to be a bill coming due. Making your payments on time can be tough when you’re having financial troubles or simply juggling a lot of responsibilities. It’s important to pay your bills on time to protect your credit health. Late payments can be reported to the credit bureaus, appear on your credit report and negatively impact your credit scores for up to seven years.

Security Boulevard
JANUARY 31, 2021
Many thanks to BSidesSF and Conference Speakers for publishing their outstanding presentations; of which, originally appeared at the organization's BSidesSF 2020 , and on the DEF CON YouTube channel. Additionally, the BSidesSF 2021 will take place on March 6 - 9, 2021 - with no cost to participate. Enjoy! Permalink. The post BSidesSF 2020 – Ari Eitan’s ‘Mapping The Connections Inside Russia’s APT Ecosystem’ appeared first on Security Boulevard.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
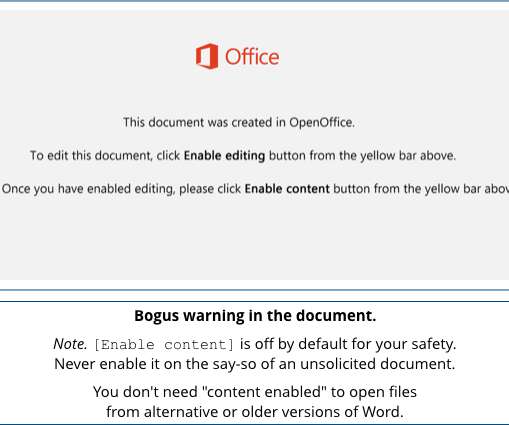
Naked Security
JANUARY 31, 2021
Great news from Europol - if you've heard of Emotet, you'll have a good idea how badly things often end for its victims.

Security Boulevard
JANUARY 31, 2021
Cyber attacks that lead to data breaches are becoming increasingly common in all industries, but there are certain types of businesses that are more vulnerable than others. The hospitality industry in particular is one of the most likely industries to be targeted by cybercriminals in addition to retail and finance. It only makes sense that […]… Read More.

CyberSecurity Insiders
JANUARY 31, 2021
In coming days, all you WhatsApp users out there interested in making a login through a desktop or a web app will have to go through a biometrics security login feature where-in users need to authenticate themselves with a fingerprint, face or Iris scan. However, all depends on the device capabilities and will be besides the existing QR Code authentication found in the settings feature of the mobile app.
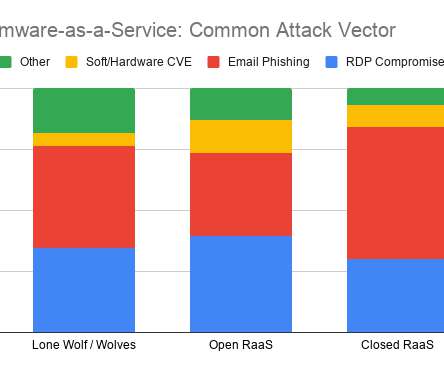
Security Boulevard
JANUARY 31, 2021
Coveware’s Q4 Ransomware Report finds that fewer companies are paying. criminal extortionists that are holding stolen data for ransom. The post Ransomware Payments Fall as Fewer Companies Pay Data Exfiltration Extortion Demands appeared first on Security Boulevard.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

CyberSecurity Insiders
JANUARY 31, 2021
Digital Certificates are virtual IDs that represent users, machines, servers, and the like in the digital landscape. A user’s attributes can be input onto a certificate and issued to that user’s device, verifying that user’s identity whenever they access the network. Digital Certificates are vastly superior mechanisms of authentication security when compared to passwords because they use the power of Public Key Cryptography.
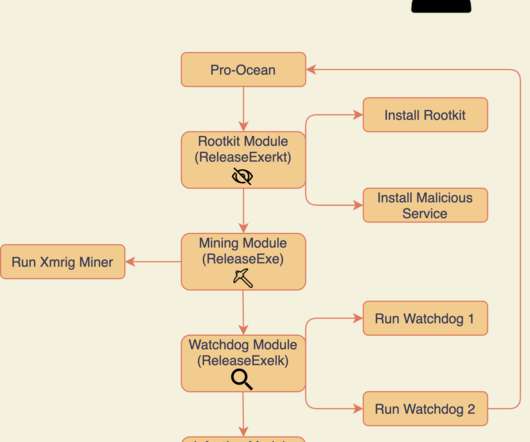
Security Affairs
JANUARY 31, 2021
The Rocke group is using a new piece of cryptojacking malware dubbed Pro-Ocean to target Apache ActiveMQ, Oracle WebLogic, and Redis installs. The cybercrime group Rocke is using a new piece of cryptojacking malware called Pro-Ocean to target vulnerable Apache ActiveMQ, Oracle WebLogic, and Redis intalls. The malware is an evolution of a Monero cryptocurrency miner that was first spotted by Unit 42 researchers in 2019.

CyberSecurity Insiders
JANUARY 31, 2021
Technology Giant Apple Inc has added a new security update that helps to secure iPhones and iPads against cyber attacks launched through iMessages. Officially dubbed as BlastDoor, the feature acts as a security system to curtail malicious messages from reaching the users. Google Project Zero Team was the first to discover the new update pushed onto the devices loaded with iOS 14 OS.

Security Boulevard
JANUARY 31, 2021
Earlier this week, Ince, the international legal and professional services firm, in cooperation with Mission Secure, launched a new integrated cybersecurity solution for the maritime sector as part of what is called Ince Maritime. This cooperation offers the industry’s first integrated cybersecurity legal advisory, business consultancy, and technology offering helping ship owners and operators navigate the sector’s greatest challenges and IMO 2021 cyber compliance.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Affairs
JANUARY 31, 2021
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the international press subscribe here. Chipmaker Intel reveals that an internal error caused a data leak Hacker leaks data of 2.28M users of dating site MeetMindful Tesla sues former employee for allegedly stealing sensitive docs Cryptocurrency exchange BuyUcoin hacked, data of 325K+ users leaked Cryptomin

Security Boulevard
JANUARY 31, 2021
via the respected information security capabilities of Robert M. Lee & the superlative illustration talents of Jeff Haas at Little Bobby Comics. Permalink. The post Robert M. Lee’s & Jeff Haas’ Little Bobby Comics – ‘WEEK 314’ appeared first on Security Boulevard.

Trend Micro
JANUARY 31, 2021
IDC analyst, Michael Suby, explains the importance of upgrading XDR security integrations.

Security Boulevard
JANUARY 31, 2021
Many thanks to BSidesSF and Conference Speakers for publishing their outstanding presentations; of which, originally appeared at the organization's BSidesSF 2020 , and on the DEF CON YouTube channel. Additionally, the BSidesSF 2021 will take place on March 6 - 9, 2021 - with no cost to participate. Enjoy! Permalink. The post BSidesSF 2020 – Byron Roosa’s ‘A Look At Jython-Enhanced Reverse Engineering With Ghidra’ appeared first on Security Boulevard.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Trend Micro
JANUARY 31, 2021
Our CVE Story: Learning to Embrace Recognition and Mitigations of Vulnerabilities as a Strength.

Security Boulevard
JANUARY 31, 2021
An interesting new set of evidence shows an old controversial theory is turning out to be true: Ronald Reagan worked covertly to block American attempts to free their hostages in Iran, as a means to win the Presidency. A Jacobin magazine article writes up the core issue: [we don’t have a smoking gun for] Reagan … Continue reading New Data Proves Reagan Scuttled Iran Embassy Hostage Release — Harmed America to Win Election ?.

CyberSecurity Insiders
JANUARY 31, 2021
An increase in ransomware attacks is not news to us anymore. However, that number has risen dramatically in 2020, a trend that businesses and individuals alike must NOT ignore. Back in 2019, a McAfee report confirmed that across all sectors, ransomware incidents increased by 118% during the first quarter of 2019. That number spiked significantly in 2020, where a Mid-Year Threat Landscape Report 2020 from Bitdefender shows a 715% year over year increase in detected and blocked ransomware attacks

Security Boulevard
JANUARY 31, 2021
A new report highlighted in Security Boulevard, is showing a 51 percent increase in attacks on web applications hosted by healthcare providers during December 2020, the timing of which coincides with the initial distribution of COVID-19 vaccines. The post Attacks on Healthcare Applications Increased in December 2020 appeared first on K2io. The post Attacks on Healthcare Applications Increased in December 2020 appeared first on Security Boulevard.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

CyberSecurity Insiders
JANUARY 31, 2021
Regardless of how familiar you are with Information Security, you’ve probably come across the term ‘malware’ countless times. From accessing your business-critical resources and sensitive information to halting business operations and services, a malware infection can quickly become an organization’s worst nightmare come true. As a business owner, you must be aware of the implications of different types of malware on your company’s bottom line, and what steps you can take to protect your company

Spinone
JANUARY 31, 2021
The article was updated in February 2021. What makes the best backup tool for your O365 data? There are many factors to this, but the main ones are: Automation and frequency Recovery speed and accuracy Security and compliance of a service Following the best backup practices A user-friendly all-in-one admin panel Swift search The lack of a single feature from the list can significantly worsen your experience with a backup service.

CyberSecurity Insiders
JANUARY 31, 2021
The industry is at a pivotal point. With the pandemic driving up work-from-home and forcing hybrid work environments as well as many applications moving to the cloud, cybersecurity professionals are challenging best practices and once-thought foundational assumptions. Is a platform with tightly integrated native capabilities the right foundation for the future security instead of siloed security tools?
Let's personalize your content