
News, news analysis, and commentary on the latest trends in cybersecurity technology.
The group that shut down the second largest city in Greece was not new but a relaunch of DoppelPaymer.

In July 2021, the second largest city in Greece fell victim to a cyberattack orchestrated by an apparently amateur ransomware group. PayOrGrief appeared to have existed for just a couple of weeks when it broke through Thessaloniki's security systems.
The group exfiltrated and encrypted numerous files before issuing a devastating $20 million ransom demand. Unsure of just how far the breach went, the municipality's security team was forced to shut down all of the Thessaloniki website's public-facing services and launch a full investigation into the breach before it could even consider whether to pay the immense ransom.
Spot the Difference: PayOrGrief and DoppelPaymer
It didn't take long for PayOrGrief to gain a reputation for disruption. Its use of double extortion ransomware tactics has proved effective in targeting organizations in all kinds of industries, including numerous manufacturers and municipalities like Thessaloniki.
The novelty of PayOrGrief's operation made it easy for it to beat security tools based on historical attacks, particularly in those first few weeks. Security experts had their suspicions, however, that PayOrGrief was more than the latest budding group to join the ransomware scene. Its attack playbook suggested experience.
Further investigations more or less confirmed that PayOrGrief was not a new group but a rebrand of an older one called DoppelPaymer, which ended its operations in May 2021. With the new PayOrGrief moniker and a slightly shifted set of tactics, techniques, and procedures (TTPs), the group has seen success to the tune of over $10 million in ransom payments.
The success of the PayOrGrief rebrand demonstrates just how easily a group can obscure itself from the sight of tools based on historical data. Altering its TTPs allowed PayOrGrief to beat security tools, but these changes were far from substantial, and for analysts the DoppelPaymer playbook was still plain to see.
How PayOrGrief Orchestrates an Attack
This playbook was thrown open when, in July 2021, PayOrGrief targeted a European manufacturing company. The company in question had deployed Darktrace's self-learning artificial intelligence (AI) technology, which was continuously updating its understanding of the digital business and looking for anomalous behavior indicative of a threat. This technology was able to reveal the life cycle of PayOrGrief's attack.
PayOrGrief often begins its attacks with phishing emails containing fake updates or malicious documents through which it can inject malware strains like Dridex into target devices. In this case, four devices were compromised, likely by a single phishing campaign, and began to make command-and-control (C2) connections to several rare external IPs.
These connections, encrypted with an invalid SSL certificate, were followed by a 50MB upload of data to the company's corporate server. With this escalated position, the attackers established keep-alive beacons and were then ready to begin the exfiltration stage of this double extortion ransomware attack.
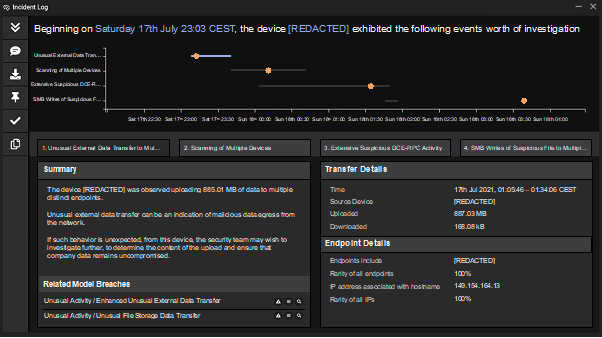
AI-generated summary of the incident, showing the data exfiltration from a single device. (Source: Darktrace)
In just a few hours, over 100GB of data was exfiltrated via HTTPS to the file storage platform Mega. The attackers had targeted more than this, but the company's autonomous defenses stood in their way.
Having recognized that this behavior was highly unusual in the context of the business' normal "pattern of life," the AI could have stopped the threat at its earliest stages if not mostly blocked from intervening by the company's configuration settings. The AI took what limited action it had permission to and limited the scope of the data exfiltration. By detecting and blocking anomalous file activity, it obstructed some of the exfiltration efforts, while continuing to monitor those parts of the digital estate in which it couldn't take direct action.
The attackers continued to move laterally through the digital estate, using RDP and SMB for internal reconnaissance and exploiting administrative privileges and processes. And then, only 10 hours after the first compromised devices began making malicious connections, PayOrGrief deployed its ransomware.
Encryption spread through the company, with an SMB write with the ".pay0rgrief" file extension seen on 137 devices. Once again, the AI cybersecurity system was able to protect certain devices from anomalous file activities and narrow the scope of the attack considerably. Through each stage of the attack — including C2, lateral movement, internal reconnaissance, exfiltration, and encryption — the AI suggested actions to block specific connections and enforce devices' patterns of life in order to halt the threat without disrupting the business itself.
Stopping the Next Big Name in Ransomware
PayOrGrief is no longer an unfamiliar name, a fact that will now be reflected in the OSINT of many rules-based cybersecurity solutions. But if organizations continue with this approach, looking at historical attacks and playing continual catch-up with the latest ransomware strains and TTPs, they will always be vulnerable to whatever is coming next. As the speed and efficacy of the DoppelPaymer rebrand demonstrates, focusing on the specificities of the attacker is a short-sighted solution.
Businesses should instead adopt cybersecurity tools that stop threats regardless of whether they have been seen before. By continuously updating their understanding of how your business should behave normally, AI-driven solutions like Darktrace can piece together anomalies to detect emerging attacks and even take autonomous action to stop them. That means no matter what they call themselves, or how they operate, attackers will be seen for what they are — and stopped.
About the Author(s)
You May Also Like
Defending Against Today's Threat Landscape with MDR
April 18, 2024The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024