Trends in Developing a New Cyber Workforce Strategy
Lohrman on Security
SEPTEMBER 18, 2022
White House efforts to strengthen the cybersecurity workforce nationwide took several new steps forward over the past few months.

Lohrman on Security
SEPTEMBER 18, 2022
White House efforts to strengthen the cybersecurity workforce nationwide took several new steps forward over the past few months.

SecureBlitz
SEPTEMBER 18, 2022
For those currently working on metaverse creation, we strongly recommend that you address the issues of protection against DDoS attacks and resilience to DDoS impacts in advance. Otherwise, there is a high probability that one day these metaverses will literally collapse in front of many thousands or even millions of their users. Metaverses – At […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Bleeping Computer
SEPTEMBER 18, 2022
Enhanced Spellcheck features in Google Chrome and Microsoft Edge web browsers transmit form data, including personally identifiable information (PII) and in some cases, passwords, to Google and Microsoft respectively. [.].
Security Boulevard
SEPTEMBER 18, 2022
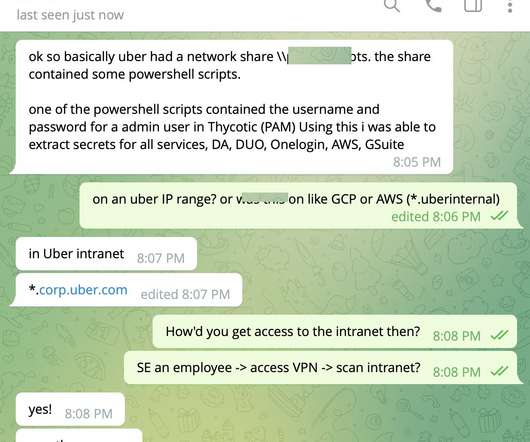
Reading Time: 6 minutes On Thursday, September 15, Uber, the ride-sharing giant, had a security incident after reports claimed a hacker had breached its internal network. Uber joins the ranks of other organizations, with 45% of businesses having experienced a cloud-based data breach over the past year. Uber’s current data breach is severe and wide-ranging, spreading access across their […].

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Affairs
SEPTEMBER 18, 2022
The Password management solution LastPass revealed that the threat actors had access to its systems for four days during the August hack. Password management solution LastPass shared more details about the security breach that the company suffered in August 2022. The company revealed that the threat actor had access to its network for four days in August 2022.

Security Boulevard
SEPTEMBER 18, 2022
White House efforts to strengthen the cybersecurity workforce nationwide took several new steps forward over the past few months. The post Trends in Developing a New Cyber Workforce Strategy appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

WIRED Threat Level
SEPTEMBER 18, 2022
Snipers on buildings. Drone no-fly zones. Temporary CCTV. The security plan is even more complex than it was for the London 2012 Olympics.

Security Boulevard
SEPTEMBER 18, 2022
Our sincere thanks to BSidesLV for publishing their outstanding conference videos on the organization's YouTube channel. Permalink. The post BSidesLV 2022 Lucky13 BreakingGround – Jonathan Leitschuh’s And Patrick Way’s ‘Scaling The Security Researcher To Eliminate OSS Vulnerabilities Once And For All’ appeared first on Security Boulevard.
WIRED Threat Level
SEPTEMBER 18, 2022
Tired of advertisers spying on your private communications? This beta promises to kick tracking technology to the curb.

Security Boulevard
SEPTEMBER 18, 2022
Part 1: Why Storage Managers Need to Prepare for the Ransomware Scourge Certain parts of the enterprise are more concerned about ransomware than others. The security, The post The Storage Manager’s Quick-Guide to Ransomware Resiliency appeared first on Continuity™. The post The Storage Manager’s Quick-Guide to Ransomware Resiliency appeared first on Security Boulevard.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Naked Security
SEPTEMBER 18, 2022
Chester Wisniewski on what we can learn from Uber: "Just because a big company didn't have the security they should doesn't mean you can't.".

Security Affairs
SEPTEMBER 18, 2022
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the newsletter with the international press subscribe here. LastPass revealed that intruders had internal access for four days during the August hack CISA adds Stuxnet bug to its Known Exploited Vulnerabilities Catalog Bitdefender releases Universal LockerGoga ransomware decryptor North Korea-linked APT spr
Let's personalize your content