Colorado Passes Consumer Privacy Law
Schneier on Security
JULY 15, 2021
First California. Then Virginia. Now Colorado. Here’s a good comparison of the three states’ laws.

Schneier on Security
JULY 15, 2021
First California. Then Virginia. Now Colorado. Here’s a good comparison of the three states’ laws.

Tech Republic Security
JULY 15, 2021
IT and OT environments are increasing targets and threat actors are using Dark Web forums to launch cybercrimes, according to Accenture's 2021 Cyber Threat Intelligence report.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

We Live Security
JULY 15, 2021
If you'll be watching Sports Streaming events on your SmartTV, laptop, tablet or cell phone, learn the tips to keep you and your personal data safe. The post Sports events and online streaming: prepare your cybersecurity appeared first on WeLiveSecurity.

Tech Republic Security
JULY 15, 2021
Android 12 adds killswitches for both the mic and camera. Jack Wallen shows you how to add them and use them.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.
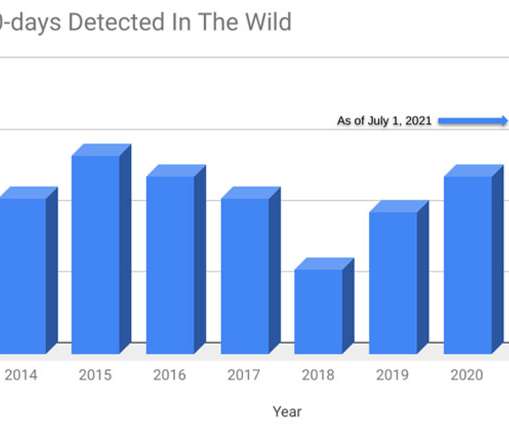
The Hacker News
JULY 15, 2021
Threat intelligence researchers from Google on Wednesday shed more light on four in-the-wild zero-days in Chrome, Safari, and Internet Explorer browsers that were exploited by malicious actors in different campaigns since the start of the year.
Tech Republic Security
JULY 15, 2021
Security experts recommend looking for increased activity from illicit mining on corporate networks when cryptocurrency prices go up.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
JULY 15, 2021
The author of a popular software-defined radio (SDR) project has removed a "backdoor" from radio devices that granted root-level access. The backdoor had been, according to the author, present in all versions of KiwiSDR devices for the purposes of remote administration and debugging. [.].

Security Boulevard
JULY 15, 2021
Cybersecurity threats are rising fast, leading enterprises that build applications to look more closely at security measures built on precautionary principles, including threat modeling, which has become core to ensuring applications can withstand future attacks. However, a recent study from Security Compass found just 25% of organizations surveyed conduct threat modeling during the early phases.

Bleeping Computer
JULY 15, 2021
?The ransomware gang behind the highly publicized attack on CD Projekt Red uses a Linux variant that targets VMware's ESXi virtual machine platform for maximum damage. [.].

Security Affairs
JULY 15, 2021
HelloKitty ransomware gang is using a Linux variant of their malware to target VMware ESXi virtual machine platform. A Linux variant of the HelloKitty ransomware was employed in attacks against VMware ESXi systems. The move of the ransomware gang aims at expanding the operations targeting enterprises that are largely adopting virtualizing platforms.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

CyberSecurity Insiders
JULY 15, 2021
While you may never have stopped to consider it, the nature of EMV banking cards has had a fundamental impact on the way we make payments over the past decades. From providing your signature after every payment to chip and pin, to mobile wallet and contactless transactions , the way we purchase goods and services is always developing to give customers an easier, more convenient shopping experience.

Bleeping Computer
JULY 15, 2021
Microsoft has addressed the Windows 10 printing issues caused by changes introduced in the June 2021 cumulative update preview with an update issued during this month's Patch Tuesday. [.].

CyberSecurity Insiders
JULY 15, 2021
As most of the Australian organizations are silently paying ransomware payments to get back access to their encrypted data, it has started a vicious cycle that has led the world to a position where it is facing a tsunami of cyber crimes. According to a finding made by Cybersecurity firm Crowdstrike there has been a 60% increase in ransomware attacks on Australian firms in the past one year and the percentage is expected to double or quadruple within next 3 years.

Bleeping Computer
JULY 15, 2021
Microsoft's print nightmare continues with another example of how a threat actor can achieve SYSTEM privileges by abusing malicious printer drivers. [.].

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
JULY 15, 2021
Small and mid-sized businesses are able to manage their information security, including web application security, in a very direct fashion. The numbers of assets, vulnerabilities, and incidents are low enough for the security manager to be able to have a clear view of IT security. Read more. The post Cybersecurity metrics for web applications appeared first on Acunetix.

Cisco Security
JULY 15, 2021
Scratch two things off the list! The Center for Internet Security (CIS) recently dropped the number of Critical Controls from 20 to 18. Some of us still think of them as the SANS Top 20, so that’s kind of a big deal. There really aren’t fewer things to do, of course. CIS updated the Controls to better address modern technology and to help you prioritize.

Security Boulevard
JULY 15, 2021
If you follow software development best practices, you’ve probably written quite a few tests for your code. Unit tests, integration tests, smoke tests, black-box tests, and maybe even end-to-end (E2E) tests. The post How to Fix Your Failing End-to-End Tests? appeared first on Security Boulevard.

Bleeping Computer
JULY 15, 2021
Microsoft and Citizen Lab have linked Israeli spyware company Candiru (also tracked as Sourgum) to new Windows spyware dubbed DevilsTongue deployed using now patched Windows zero-day vulnerabilities. [.].

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Affairs
JULY 15, 2021
Security researchers have linked a new ransomware strain called Diavol to the Wizard Spider threat group behind the Trickbot botnet. BleepingComputer noted the ransomware families utilize the same I/O operations for file encryption queueing and use nearly identical command-line parameters for the same functionality. There may be some similarities, but as they’ve explained and SpearTip has validated, there are two interesting differences that make the direct connection improbable.
Security Boulevard
JULY 15, 2021
Scanning your code base frequently to discover security risk early in development gives engineers more time time to address issues. But security risk is a challenging issue and most developers need more than just time. Consider: Over 60% of identified vulnerabilities aren’t fixed. It takes ~three months to address an identified vulnerability. These facts mean that AppSec teams can become easily overwhelmed, leaving security issues untouched and your application vulnerable.

Adam Shostack
JULY 15, 2021
Earlier this week, NIST released a Recommended Minimum Standard for Vendor or Developer Verification of Code. I want to talk about the technical standard overall, the threat modeling component, and the what the standard means now and in the future. To summarize: new requirements are coming to a project near you, and getting ready now is a good idea.
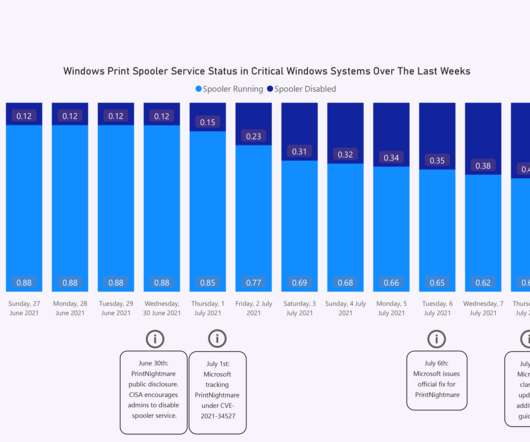
Security Boulevard
JULY 15, 2021
The Infamous Windows Print Spooler Service Hit Again During June’s 2021 Patch Tuesday, Microsoft addressed a minor local privilege escalation (LPE) vulnerability (CVE-2021-1675) in the Windows Print Spooler service (spoolsv.exe), which is responsible for printing management in Windows. Almost two weeks later, the vulnerability impact was changed from LPE to Remote Code Execution (RCE) after […].

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Bleeping Computer
JULY 15, 2021
Microsoft is sharing mitigation guidance on a new Windows Print Spooler vulnerability tracked as CVE-2021-34481 that was disclosed tonight. [.].

Security Boulevard
JULY 15, 2021
Technology is becoming more effective at early ransomware detection. Solutions can often automatically shut down attacks and minimize the damage. It is reasonable to conclude, however, that there is no truly impenetrable ransomware defense. The more complete answer lies in recovery. Maintaining pristine datasets that are more readily restored, minimizing loss while preserving data integrity, The post Disrupting Ransomware with Advanced File System Techniques appeared first on Security Boulevard.

Elie
JULY 15, 2021
Learn the concepts behind deep-learning side-channels attack, a powerful cryptanalysis technique, by using it to recover AES cryptographic keys from a hardware device.

Bleeping Computer
JULY 15, 2021
WooCommerce, the popular e-commerce plugin for the WordPress content management system has been updated to patch a serious vulnerability that could be exploited without authentication. [.].

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Boulevard
JULY 15, 2021
Nozomi Networks Labs has produced a new OT/IoT security report. Don’t miss this summary of vulnerability trends as well as important information about ransomware and IoT security camera threats. The post New Report: Ransomware, Vulnerabilities and IoT Security Threats appeared first on Nozomi Networks. The post New Report: Ransomware, Vulnerabilities and IoT Security Threats appeared first on Security Boulevard.
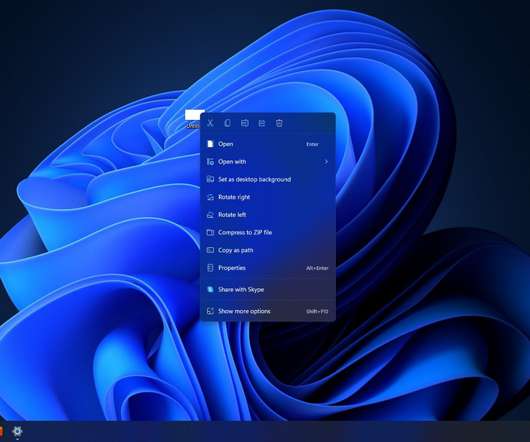
Bleeping Computer
JULY 15, 2021
Windows 11 preview build 22000.71 is now live in the Dev Channel of the Windows Insider program and it comes with visual improvements for the context menu and various right-click menus. [.].

Elie
JULY 15, 2021
Learn how to perform a deep-learning side-channels attack using TensorFlow to recover AES cryptographic keys from a hardware device power traces, step by step.

CSO Magazine
JULY 15, 2021
Dan Bowden had the right mix of experience and credentials to land his next CISO post, but he wanted to make sure his resume reflected that fact.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content