Weekly Update 266
Troy Hunt
OCTOBER 23, 2021
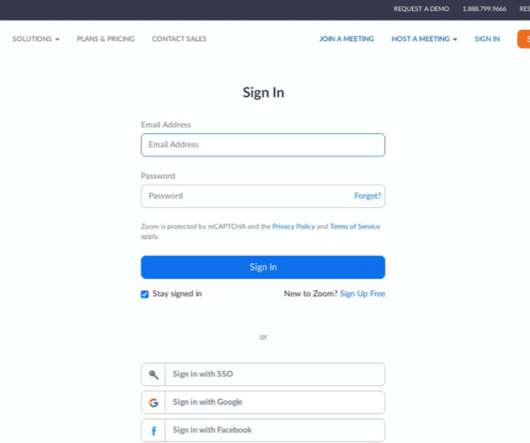
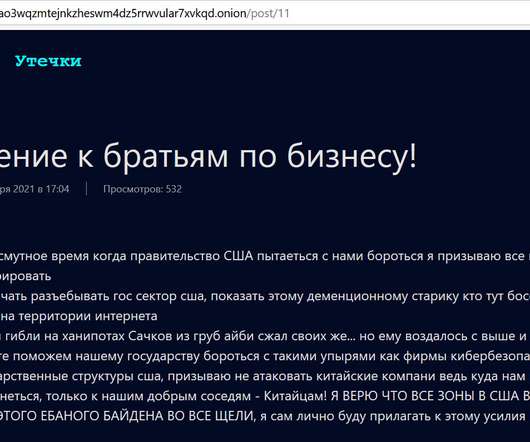
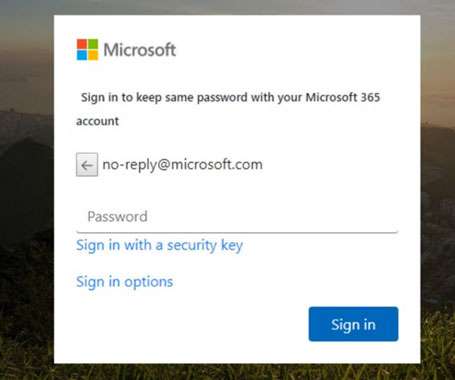
Well this is a totally different office view! I'm properly getting into working more on the acoustics and aesthetics to make this the most productive environment possible which means this week things are in a bit of disarray due to ongoing works. Speaking of disarray, I've not been able to raise this week's sponsor in time so as I say in the video, their appearance on my blog this week is a bit. unusual.






















Let's personalize your content