Weekly Update 282
Troy Hunt
FEBRUARY 12, 2022
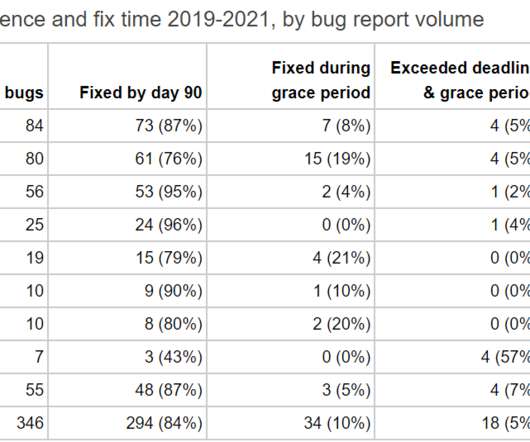
Just listening back to this now, I'm really happy with the Focusrite Scarlett Solo DAC that has replaced the old setup. Super simple, one of the cheapest of all the options and just works! Good times. The other thing of note as I put this video into a blog post is that I definitely want to carve out time to write up that DigiCert blog post I discussed.

















Let's personalize your content