Microsoft Teams phishing campaign targeted up to 50,000 Office 365 users
Security Affairs
OCTOBER 24, 2020
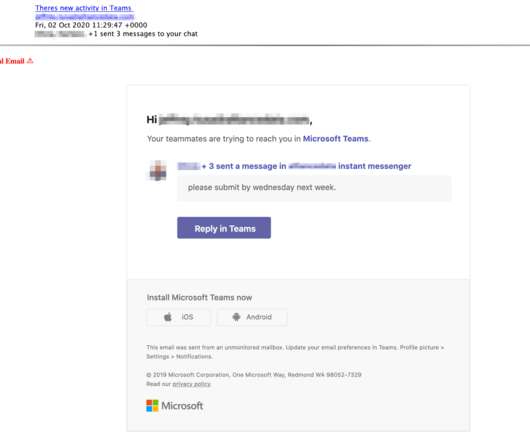
Experts warn of a phishing campaign that already targeted up to 50,000 Office 365 users with a fake automated message from Microsoft Teams. Secruity researchers reported that up to 50,000 Office 365 users have been targeted by a phishing campaign that pretends to be automated message from Microsoft Teams. The bait message uses fake notifications of a “missed chat” from Microsoft Teams, the campaigns aims at stealing Office 365 recipients’ login credentials.










Let's personalize your content