No, I Did Not Hack Your MS Exchange Server
Krebs on Security
MARCH 28, 2021
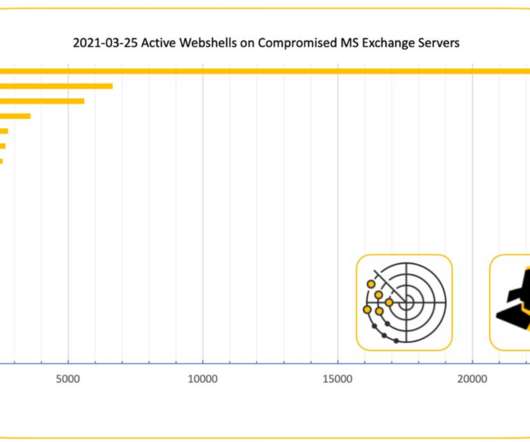
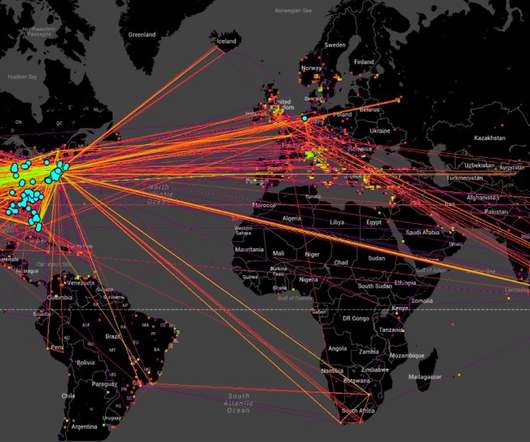
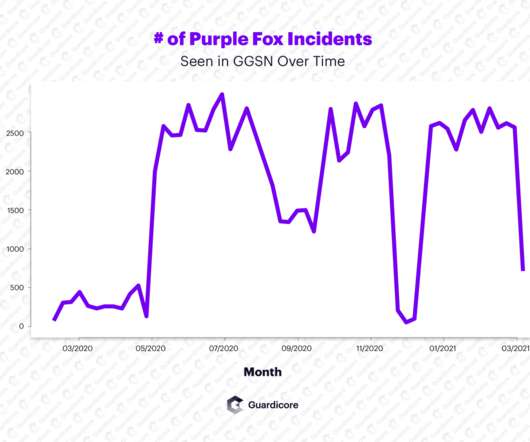
New data suggests someone has compromised more than 21,000 Microsoft Exchange Server email systems worldwide and infected them with malware that invokes both KrebsOnSecurity and Yours Truly by name. Let’s just get this out of the way right now: It wasn’t me. The Shadowserver Foundation , a nonprofit that helps network owners identify and fix security threats , says it has found 21,248 different Exchange servers which appear to be compromised by a backdoor and communicating with brian






































Let's personalize your content