Microsoft Exchange servers hacked in internal reply-chain attacks
Bleeping Computer
NOVEMBER 20, 2021
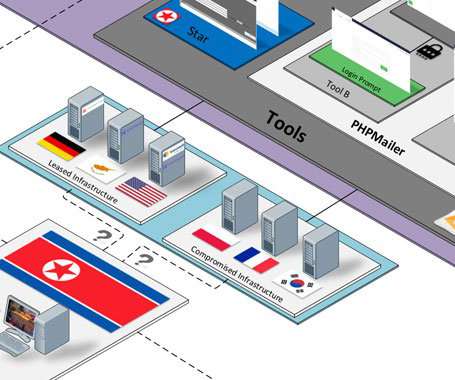
Threat actors are hacking Microsoft Exchange servers using ProxyShell and ProxyLogon exploits to distribute malware and bypass detection using stolen internal reply-chain emails. [.].























Let's personalize your content