Thoughts on the OWASP Top 10 2021
Daniel Miessler
SEPTEMBER 12, 2021
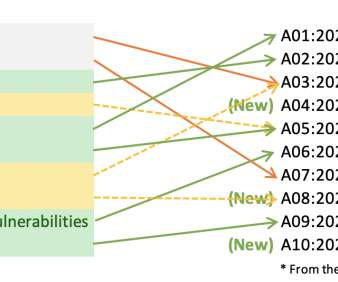
This post will talk about my initial thoughts on The OWASP Top 10 release for 2021. Let me start by saying that I have respect for the people working on this project, and that as a project maintainer myself, I know how impossibly hard this is. Right, so with that out of the way, here’s what struck me with this list, along with some comments on building lists like this in general.



































Let's personalize your content