Lightning Cable with Embedded Eavesdropping
Schneier on Security
SEPTEMBER 7, 2021
Normal-looking cables (USB-C, Lightning, and so on) that exfiltrate data over a wireless network. I blogged about a previous prototype here.

Schneier on Security
SEPTEMBER 7, 2021
Normal-looking cables (USB-C, Lightning, and so on) that exfiltrate data over a wireless network. I blogged about a previous prototype here.

Tech Republic Security
SEPTEMBER 7, 2021
Does your company need a head of data privacy, a data breach response plan, blockchain technology or something else to keep its data safe? Here are some challenges and recommendations.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CSO Magazine
SEPTEMBER 7, 2021
COVID-19 has changed the face of security forever. The perimeter defense model, which had been slowly crumbling, has now been shattered. Employees are working from home, many of them permanently. Applications are shifting to the cloud at an accelerating pace. Enterprise security today is all about secure remote access and protecting cloud-based assets.
Security Boulevard
SEPTEMBER 7, 2021
In this OSINT analysis I'll offer in-depth information and analysis of Bulgaria's Bulgarian Cyber Army including personally identifiable information on some of the key members behind the group for the purpose of assisting U.S Law Enforcement and the U.S Intelligence Community on its way to track down and prosecute the cybercriminals behind these campaigns.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

We Live Security
SEPTEMBER 7, 2021
ESET researchers have investigated a targeted mobile espionage campaign against the Kurdish ethnic group, and that has been active since at least March 2020. The post BladeHawk group: Android espionage against Kurdish ethnic group appeared first on WeLiveSecurity.

Security Boulevard
SEPTEMBER 7, 2021
Amazon, Apple and Google will have their days in court, charged with listening to your conversations when you least expect it. The post Alexa, OK Google, Siri—Sued for Spying appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

We Live Security
SEPTEMBER 7, 2021
Following the incident the company has updated its website and privacy policy to clarify its legal obligations to its userbase. The post ProtonMail forced to log user’s IP address after an order from Swiss authorities appeared first on WeLiveSecurity.

Bleeping Computer
SEPTEMBER 7, 2021
The Ragnar Locker ransomware group is warning that they will leak stolen data from victims that contact law enforcement authorities, like the FBI. Ragnar Locker has previously hit prominent companies with ransomware attacks, demanding millions of dollars in ransom payments. [.].

CyberSecurity Insiders
SEPTEMBER 7, 2021
Most Americans are having a habit of storing their ATM pins, bank account details and, to a certain extent, debit/credit card numbers on mobiles, computers and emails. And this is paving way to the rise in financial frauds says a survey conducted by MasterCard USA. A similar survey conducted by a firm Unisys claims that most of the finance related frauds are taking place as online shoppers are posting or giving away their card details online or on call that can be misused by cyber crooks for cyb

Bleeping Computer
SEPTEMBER 7, 2021
Microsoft today shared mitigation for a remote code execution vulnerability in Windows that is being exploited in targeted attacks against Office 365 and Office 2019 on Windows 10. [.].

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Graham Cluley
SEPTEMBER 7, 2021
The Ragnar Locker group, a gang of cybercriminals behind a series of costly ransomware attacks against companies, has warned victims that they should not seek the assistance of law enforcement agencies.

Bleeping Computer
SEPTEMBER 7, 2021
ug in the McDonald's Monopoly VIP game in the United Kingdom caused the login names and passwords for the game's database to be sent to all winners. [.].

eSecurity Planet
SEPTEMBER 7, 2021
Zero day threats can be the source of some of the most dangerous kinds of cyberattacks. Zero day attacks take advantage of vulnerabilities that haven’t been discovered or are not publicly known yet. One of the things that makes these threats so dangerous is that they often come without warning, posing a huge risk to the companies or individuals at stake.

CSO Magazine
SEPTEMBER 7, 2021
The ATT&CK framework , developed by MITRE Corp., has been around for five years and is a living, growing document of threat tactics and techniques that have been observed from millions of attacks on enterprise networks. The funky acronym stands for Adversarial Tactics, Techniques, and Common Knowledge. It began as an internal project and morphed into this behemoth of a public knowledge base that numerous security vendors and consultants have picked up.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
SEPTEMBER 7, 2021
In the midst of the high-profile prosecution of Virgil Griffith, who is being tried in federal court for assisting North Korea in evading sanctions, the Department of Justice informed judge Kevin Castel of the Southern District of New York (SDNY) that the case evidence had been accessed by unauthorized FBI employees. Three FBI analysts and. The post Palantir Misconfiguration Allowed Unauthorized FBI Access appeared first on Security Boulevard.

PCI perspectives
SEPTEMBER 7, 2021
As small and medium businesses begin to re-open following the pandemic, it’s important to do so securely in order to protect customer’s payment card data. Too often, data breaches happen as a result of vulnerabilities that are entirely preventable. The PCI Security Standards Council (PCI SSC) has developed a set of payment protection resources for small businesses.

Security Boulevard
SEPTEMBER 7, 2021
Lt. Colonel (Ret.) Bill Hagestad examines how China's culture and troubled history of western colonialism influenced its government views and actions regarding the global internet and its interactions with western technology companies such as Google and Nortel - check it out. The post Malicious Life Podcast: Understanding China’s Cyber Culture appeared first on Security Boulevard.

CyberSecurity Insiders
SEPTEMBER 7, 2021
Facebook is intending to ban cryptocurrency related advertisements on its platform from November 2021, as they are leading to online scams and money loss schemes targeting to thousands of individuals using Facebook irrespective of their age. Charles Randell, the chairperson of UK’s Financial Conduct Authority(FCA) confirmed the news and urged all internet giants like Google & Twitter to block all crypto related scams on their sites.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
SEPTEMBER 7, 2021
A recently fixed WhatsApp security vulnerability that, if exploited, could cause data leakage underscores the fact that hackers can bypass end-to-end encryption with some machinations. WhatsApp included a patch for the flaw in its February 2021 Security Advisory Report and, in a statement, assured Check Point researchers Dikla Barda and Gal Elbaz—who analyzed the Out-Of-Bounds.

The Hacker News
SEPTEMBER 7, 2021
The maintainers of Jenkins—a popular open-source automation server software—have disclosed a security breach after unidentified threat actors gained access to one of their servers by exploiting a recently disclosed vulnerability in Atlassian Confluence service to install a cryptocurrency miner.

Security Boulevard
SEPTEMBER 7, 2021
The network perimeter—as it is traditionally understood—is dead. Firewalls were once considered the pinnacle of cybersecurity: erect a strong enough one around the network and everything inside will be secure. Unfortunately, that was probably never true, but it’s easy to see why the idea gained popularity. Humanity has been building walls to keep enemies at.
Tech Republic Security
SEPTEMBER 7, 2021
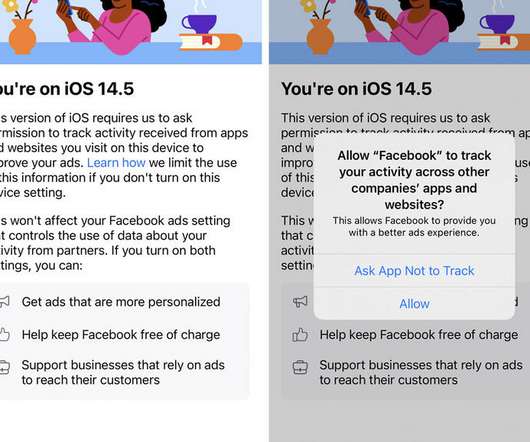
You can tell iOS and iPadOS apps not to track your activity. Here's how.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Boulevard
SEPTEMBER 7, 2021
Risk management programs require a specific approach in order to be truly effective. With threats on the rise, it’s becoming increasingly important to fast-track the development of these programs to keep organizations as secure and resilient as possible. The difference between a mature program and an undeveloped or developing program may seem obvious, but let’s[…].

Malwarebytes
SEPTEMBER 7, 2021
They say there’s two sides to every story. Depending on your point of view, you may have heard a recent story that’s either about overreaching law enforcement and protestors exposed by organisations happy to hand over revealing data despite saying they won’t. Or: BREAKING: legitimate business complies with legitimate law enforcement request. news at 6. — cje (@caseyjohnellis) September 7, 2021.

Security Boulevard
SEPTEMBER 7, 2021
HackPhreak is a well known U.S based hacking group throughout the 90's which is known to have been actively using IRC for the purpose of communicating and recruiting new members including its own Anti-Pedophile organization among the Internet's first community-driven organization to fight online child pornography launched by a popular and well-known hacking group including the following high-profile members of the group: HackPhreak Group Members Include: Bronc Buster, Lothos, Overdose, Truedog,

Malwarebytes
SEPTEMBER 7, 2021
After the uproar from users and privacy advocates about Apple’s controversial plans to scan users’ devices for photos and messages containing child abuse and exploitation media, the company has decided to put the brakes on the plan. If you may recall, Apple announced in early August that it would introduce the new capability in iOS 15, iPadOS 15, watchOS 8, and macOS Monterey.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Boulevard
SEPTEMBER 7, 2021
In this analysis I'll provide personally identifiable information on some of the key members of the infamous 29A Virus Coding Group for the purpose of assisting U.S Law Enforcement and the U.S Intelligence Community on its way to track down and prosecute the cybercriminals behind these campaigns. Personal email belonging to the group: 29A@sourceofkaos.com.

Heimadal Security
SEPTEMBER 7, 2021
Last week, multinational computer networking company Netgear released security patches to tackle three high-severity flaws impacting over 20 of its products, mostly smart switches. The flaws were found and reported to the company by security engineer Gynvael Coldwind and are tracked by the vendor as PSV-2021-0140, PSV-2021-0144, PSV-2021-0145. The three vulnerabilities received a CVSS score […].

Security Boulevard
SEPTEMBER 7, 2021
Welcome to week 2 of National Insider Threat Awareness Month! One of the things that. The post The Origin of Insider Attacks: Where do Insider Threats Come from? appeared first on Gurucul. The post The Origin of Insider Attacks: Where do Insider Threats Come from? appeared first on Security Boulevard.

Security Affairs
SEPTEMBER 7, 2021
The development team behind the Jenkins server disclose a security breach, threat actors deployed a cryptocurrency miner on one of its servers. The development team behind the Jenkins Project disclosed a security breach after threat actors compromised one of their internal servers and installed a cryptocurrency miner. Jenkins is the most popular open-source automation server, it is maintained by CloudBees and the Jenkins community.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content