Are You One of the 533M People Who Got Facebooked?
Krebs on Security
APRIL 6, 2021
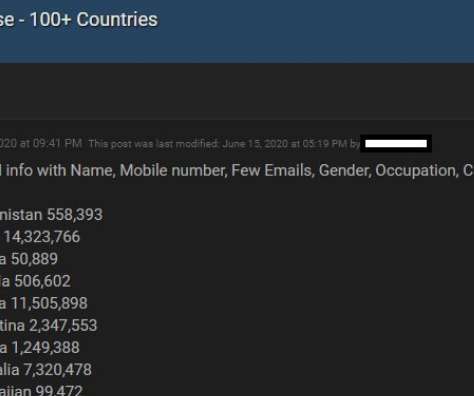
Ne’er-do-wells leaked personal data — including phone numbers — for some 553 million Facebook users this week. Facebook says the data was collected before 2020 when it changed things to prevent such information from being scraped from profiles. To my mind, this just reinforces the need to remove mobile phone numbers from all of your online accounts wherever feasible.







































Let's personalize your content